Keywords
Computer Science and Digital Science
- A1.2.3. Routing
- A1.2.4. QoS, performance evaluation
- A1.2.5. Internet of things
- A1.2.6. Sensor networks
- A1.2.7. Cyber-physical systems
- A1.2.8. Network security
- A2.3. Embedded and cyber-physical systems
- A2.3.1. Embedded systems
- A2.3.2. Cyber-physical systems
- A2.3.3. Real-time systems
- A4.5. Formal methods for security
- A4.6. Authentication
- A4.7. Access control
- A5.10.1. Design
- A5.10.3. Planning
- A5.10.5. Robot interaction (with the environment, humans, other robots)
- A5.10.6. Swarm robotics
- A9.5. Robotics
- A9.9. Distributed AI, Multi-agent
Other Research Topics and Application Domains
- B3.3.1. Earth and subsoil
- B3.5. Agronomy
- B4.5.2. Embedded sensors consumption
- B5.1. Factory of the future
- B5.4. Microelectronics
- B5.6. Robotic systems
- B6.2.2. Radio technology
- B6.2.3. Satellite technology
- B6.4. Internet of things
- B6.6. Embedded systems
- B6.7. Computer Industry (harware, equipments...)
- B8.1. Smart building/home
- B8.1.2. Sensor networks for smart buildings
- B9.1.2. Serious games
1 Team members, visitors, external collaborators
Research Scientists
- Thomas Watteyne [Team leader, INRIA, Senior Researcher, HDR]
- Filip Maksimovic [INRIA, Starting Research Position]
- Paul Mühlethaler [INRIA, Senior Researcher, HDR]
- Malisa Vucinic [INRIA, Researcher]
PhD Students
- Razane Abu-Aisheh [NOKIA, CIFRE]
- Said Alvarado-Marin [Inria, from Apr 2022]
- Sara Faour [Inria, from Oct 2022]
- Haouda Ghamni [University of Gabes, Tunisia, from Sep 2022]
- Abdelhak Hidouri [University of Gabes, Tunisia, from Sep 2022]
- Iman Hmedoush [Inria, until May 2022]
- Tayssir Ismail [University of Gabes, Tunisia]
- Felix Marcoccia [Thales, CIFRE, from Apr 2022]
- Trifun Savic [WATTSON ELEMENTS]
Technical Staff
- Said Alvarado Marin [INRIA, Engineer, until Mar 2022]
- Romain Facq [Inria, Engineer, from Oct 2022]
- Felix Marcoccia [THALES, Engineer, until Feb 2022]
Interns and Apprentices
- Theo Akbas [ENSEA, Intern, from May 2022 until Aug 2022]
- Kaouther Benguessoum [ENSI, Intern, from Mar 2022 until Jul 2022]
- Cristobal Huidobro-Marin [Universidad Técnica Federico Santa María, Intern, from Jun 2022]
- Charles Thonier [ENSTA Paris, Intern, from Mar 2022 until Jul 2022]
Administrative Assistant
- Anne Mathurin [INRIA]
Visiting Scientists
- Soumya Banerjee [U. College Cork, from Nov 2022]
- Miguel Gutiérrez Gaitán [U. Porto, Portugal, from Apr 2023 until Jul 2022]
- Leila Saidane [ENSI Tunisia, from Nov 2022]
External Collaborators
- Leila Azouz Saidane [ENSI TUNIS, from Mar 2022 until Mar 2022]
- Martina Maria Balbi Antunes [IMT ATLANTIQUE]
- Soumya Banerjee [UCC CORK]
- Selma Boumerdassi [CNAM]
- Samia Bouzefrane [CNAM]
- Mohamed Elhadad [SYSTEMX]
- Éric Renault [ESIEE]
- Leila Saidane [ENSI]
2 Overall objectives
The AIO team is a leading research team in low-power wireless communications. The team is designing Tomorrow's Internet of (Important) Things. It pushes the limits of low-power wireless mesh networking by applying them to critical applications such as robotics, industrial control loops, with harsh reliability, scalability, security and energy constraints. The AIO team co-chairs the IETF 6TiSCH and IETF LAKE standardization working group and co-leads Berkeley's OpenWSN project. It is heavily involved in real-world applications, and oversees over 1,000 sensors deployed on 3 continents for smart agriculture, smart city and environmental monitoring applications. The team's research program is organized around 5 pilars: Smart Dust, Low-Power Wireless Networking, Security in Constrained Systems, Swarm Robotics and Vehicle Area Networking. The team is associated with Prof. Pister's team at UC Berkeley, working on Smart Dust.
3 Research program
The team's research program is composed of five areas of research, which we number A1 through A5. Please note that the order of the areas does not represent any sort of order of importance, or dependence.
3.1 [A1] Smart Dust
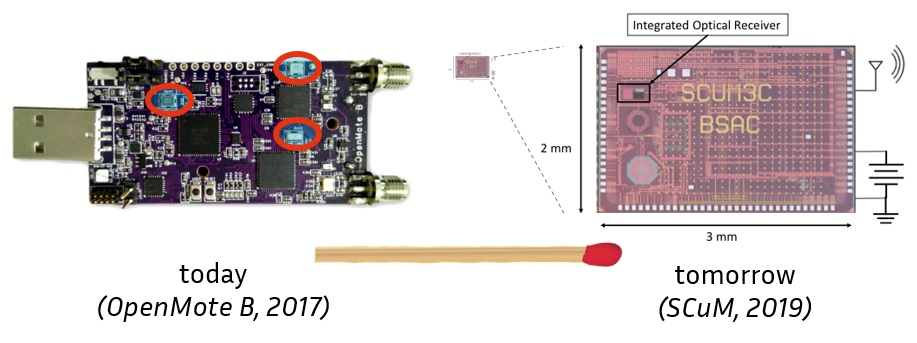
SCuM (“Single Chip Micro Mote”), depicted in Fig. 1, is the world's first crystal-free micro-mote which implements a full IEEE802.15.4 and BLE radio. It uses oscillating circuits with a 16,000 ppm drift and which are very sensitive to temperature, instead of a traditional crystal oscillator (40 ppm drift). This clock source is responsible for choosing communication frequency and modulation rate. This crystal-free approach reduces the size of the mote significantly, and will be widely adopted by the industry. While we conduct our research on SCuM, it is representative, and results carry over to other designs. We have shown anecdotally that we can manually calibrate the oscillators and have SCuM communicate with an off-the-shelf IEEE802.15.4-compliant mote. Can we create an algorithm which continuously self-calibrates the clocks on SCuM so it keeps communicating even when the temperature changes? The tools we have to answer that questions are Machine Learning and Control Theory. Can we use Machine Learning to create a static model to tune the clocks?Can we then use Control Theory to augment this into a model that dynamically tracks the clock of a neighbor node, and keeps SCuM communicating even when temperature changes? Answering these questions will lead us to implementing these solutions onto SCuM and making sure two nearby SCuM motes can communicate.
This area of research is further divided into two strands.
[A1.1] Fast Calibration and Standardization
The behavior of the oscillators within the SCuM chip is not fully understood. We have shown in CITATION NOT FOUND: suciu19experimental that the oscillators drift by up to 16,000 ppm over temperature. This is much more than the maximum 40 ppm required by the IEEE 802.15.4 standards. The challenge is hence to turn an unstable 16,000 ppm oscillator into a stable 40 ppm oscillator so SCuM chips can reliably communicate with off-the-shelf IEEE 802.15.4 and BLE transceivers, and with other SCuM chips. This may be done in the following steps:
- The first question to answer is: can we model the behavior of these oscillators? Specifically, we want to know how much of the variation of these oscillators is a function of temperature, voltage or other parameters, and how much is due to thermal noise, i.e. a random variation which cannot be controlled. A secondary goal is to turn these lessons learnt into the simplest possible model (e.g. some form of a decision tree) so it can be implemented on individual SCuM chips. We know that simple curve fitting on 2-point of 3-point calibration over temperature is usually done for crystal-oscillators, but this will most likely not work here. We adopt the approach of CITATION NOT FOUND: oroza17machine and use Machine Learning to answer both questions. Random Forest, LDA or PCA indicate the contribution of each feature to the overall model. One preliminary step is hence to gather a more complete and more annotated dataset as in CITATION NOT FOUND: suciu19experimental. We may reach out to the scikit-learn team, as well as Prof. Carlos Oroza from the University of Utah with whom we have been collaborating on ML approaches for wireless communication systems.
- There is a good possibility that the model from the study above is not able to fully characterize drift in all cases. Do we need reinforcement learning to allow micro-motes to calibrate against regular motes? In practice, we use motes from our OpenTestbed CITATION NOT FOUND: munoz19opentestbed as a “calibration box”: they are programmed to listen on all frequencies, and acknowledge any calibration probe frames they receive. The goal is to create an algorithm by which a micro-mote transmits such probes as it sweeps through calibration settings until it receives an acknowledgement and thereby knows that setting is valid for a particular frequency. The challenge is that tuning the oscillators needs to happen continuously, as any temperature change will cause SCuM to lose connectivity to the calibration box. If reinforcement learning is needed, similar to our approach in CITATION NOT FOUND: munoz19opentestbed, one option is to use game theory to model as a “Multi-Armed Bandit”, and use an -greedy algorithm to balance using the tuning parameters that worked in the past, and exploring other parameters in case the temperature has changed. The target is for uncalibrated micro-motes to self-calibrate quickly, and stay calibrated as temperature changes.
- The study above results in a protocol between a micro-mote and the calibration box. We propose this as a candidate for standardization at the IETF, possibly in the 6TiSCH working group.
Results: From a scientific point of view, A1.1 generates the world's largest open and annotated dataset of micro-mote drift, and use Machine Learning to derive a model. In case that drift model does not capture the drift fully and hence cannot ensure a micro-mote can always communicate, A1.1 also develops a dynamic fast calibration protocol against regular motes using game theory, and standardize that protocol. From a project point of view, A1.1 allows micro-motes to communicate, albeit with the help of regular motes, a necessary stepping stone for the remainder of the project.
[A1.2] The Network as a Time Source
A1.1 allows micro-motes to communicate, but does require having regular motes close to micro-motes, which puts a burden on the deployment strategy. The goal of this area is bold and ambitious: can a micro-mote use the network as a relative time reference, instead of an absolute time reference such as a crystal oscillator? This entails having a micro-mote calibrate against another micro-mote – which itself is drifting – and repeating this over a multi-hop network of micro-robots.
This goal translates into the following three studies:
- The challenge is that both neighbor nodes drift: if we were to use the approach from A1.1, neighbor nodes would lose connection. The question is: can we develop a fast-tracking algorithm which allows micro-motes to calibrate against one another? For that, we can use control theory: consider the time offset between two micro-motes as the variable, offset 0 as equilibrium, and tune the clock calibration. Similar to our approach in CITATION NOT FOUND: domingoprieto16distributed, we can use a PID controller to balance reactivity with resilience to short timing glitches. We can develop the controller in simulation by replaying its behavior against the datasets from A1.1, before implementing it on micro-motes and validating experimentally.
- In a scenario in which the micro-robots form a multi-hop mesh network, we want to avoid forming cliques of synchronized structures, given the important variation in drift between nodes. The question becomes: can we have a micro-mote calibrate against multiple neighbors at the same time? The complexity is that these neighbors can be far apart in time, so the micro-mote may need to “jump” in time depending on which neighbor it is communicating with, while implementing some averaging function that causes the network to eventually converge to a fully-synchronized state. We build upon the work published in CITATION NOT FOUND: tanaka19simulating by integrating the datasets from A1.1 into the 6TiSCH simulator, and expand the controller from the study above to support multiple neighbors.
- All TSCH networks, including 6TiSCH, build a synchronization structure inside a multi-hop mesh network rooted at a single time master, which never changes. This does not match the micro-robot application, in which all micro-robots play a similar role. The question is hence: can we build a TSCH network in which the role of time master changes from one micro-mote to another, without any disruption to the network? A corollary question is: can we imagine having multiple time masters, for example nodes equipped with crystals? We will use our previous work on the flooding-based approach from CITATION NOT FOUND: gomes16reliability, and standardize the behavioral/protocol changes through IETF 6TiSCH.
Results: From a scientific point of view, A1.2 results in deep changes to the base behavior of a TSCH protocol stack such as 6TiSCH, with a radically new way of tracking a time source neighbor, based on control theory, as well as the ability to track multiple neighbors, and have dynamic time masters. The protocol changes are standardized at the IETF. From a project point of view, A1.2 allows neighbor nodes to communicate: choose the communication frequency and the modulation/demodulation rate, and stay synchronized.
[A1.3] Wireless Enablers
Localization of individual robots in a swarm is critical for their coordination and control. Accurate localization, often implemented using visual markers and multiple cameras, is used as a ground truth to determine the accuracy of robotic control algorithms. To enable inexpensive and massive deployments of robots, we investigate lighthouse localization in conjunction with RF localization, both using angle-of-arrival techniques using antenna arrays, and ultra-wide band techniques.
The goal is summarized in the following studies:
- The first challenge involves the use of angle-of-arrival estimation using BLE transmission from the Single Chip Mote. A number of questions arise: How does the time and frequency uncertainty of the Single Chip Mote affect the accuracy of angle-of-arrival estimate?Can inaccuracies and errors caused by multipath be mitigated by using frequency diversity, both with BLE standard channels and potentially with operation outside of the ISM band?
- Lighthouse localization has already been established as a relatively accurate method to localize Single Chip Motes. However, with the addition of RF angle-of-arrival and RF localization techniques, can sensor fusion algorithms be applied to multiple measurements to both improve accuracy of the position estimate, and discard erroneous estimates caused by the mote's clock drift or unpredictable RF fading during robot movement?
- Millimeter wave (mm-wave) radios, operating at much higher frequencies than the 2.4 GHz ISM band, benefit from greater attenuation of environmental reflections, narrower beam widths when operating as phased arrays, and inherently higher spacial accuracy due to the smaller wavelength. These radios, both narrowband and wideband, have previously been used for automotive radar, range finding, and imaging. However, these solutions are rarely power constrained, unlike the devices and robots of interest to the research program. The question we contribute to address is: can low-power mm-wave radios, duty-cycled to conserve energy, be used for robotic localization? Two sub-questions arise: First, to what degree will the performance limitations set by the time and frequency imprecision of crystal-free radios affect mm-wave localization accuracy, both using narrowband and UWB rangefinding. Second, given that mm-wave radios typically burn more power when active, how deeply would such devices need to be duty-cycled to minimize the effect on battery lifetime while still improving the location estimates of large numbers of robots? The use of mm-wave radios on tiny, low-power robots also has implications for communication. Small antennas are significantly more efficient at higher frequencies. In the future, as micro-robot sizes become smaller than cm- or even mm-scales, maintaining optimal communication range will require the use of higher operating frequencies.
- Many of these studies could benefit from non-standards compliant and non-commercially available chips. To determine the effectiveness of custom RF localization solutions, we will use the Xilinx RFSoC software defined radios (SDRs) to rapidly prototype algorithms in both the 2.4 GHz and the mm-wave ISM bands. With external frequency conversion and amplification using off-the-shelf components, the same SDR can be used as a back-end for prototyping localization and communication algorithms with millimeter carriers.
Results: The results of A1.3 determine, both theoretically and practically, the performance limitations of low-power wireless devices in RF-based localization, both in the low (2.4 GHz, 5 GHz) ISM bands, and in the mm-wave ISM bands (24 GHz and 60 GHz). Furthermore, there are implications on the quality of low-power wireless networking in both power- and volume-constrained wireless devices. The extension of both localization and communication to millimeter wavelengths also generate results in small-scale ad-hoc mesh networking, which, combined with results from A2, have implications for the future of massive-scale communication for mobile wireless nodes.
3.2 [A2] Low-Power Wireless Networking
Our research has considered a large network of static motes. We see a swarm of mobile robots as a vehicle to push our networking protocols further, address all open challenges at once: mobility, latency guarantees and localization.
Let's hence assume a network of hundreds or thousands of short-range SCuM-based micro-robots moving through a cluttered building. Can we empower these micro-robots with a communication protocol stack which allows them to communicate in a dependable fashion, even as all robots are continuously moving? We define “dependable” as encompassing two things: the network guarantees end-to-end reliability (i.e. no data is lost), and timely delivery (i.e. end-to-end latency can be predicted). Time Synchronized Channel Hopping (TSCH), the low-power wireless approach used in the most demanding industrial applications today, is the ideal stepping stone because of its synchronized, scheduled, multi-hop and deterministic nature. That being said, the use case of mobile micro-robots is very different from a factory floor, and the overall stack needs to be rethought. This includes the scheduling (which cannot rely on slow explicit signaling protocols), and the multi-hop routing protocol (as coordination between micro-robots requires efficient any-to-any communication). Our team has deep protocol development, implementation, experimentation and standardization expertise. We will use control theory to dynamically adapt the schedule, resulting in predictable latency. This work will result in a complete protocol stack implementation, allowing a swarm or micro-robots to efficiently communicate.
This area of research is further divided into two strands.
[A2.1] Swarm Behavior and Mobility
The network topology of a swarm of micro-robots is dynamic because the robots move and have a short communication range. This is in stark contrast to traditional TSCH networks, which are static and stable. The question we want to answer is hence: can we use TSCH for networking a swarm of micro-robots where each node in the network is mobile? Because the state-of-the-art is very limited, answering this question requires us to reinvent both the scheduling and routing approach in a TSCH-based networking stack to support mobility.
This leads to the following three studies:
- We introduced the concept of “autonomous cells” in CITATION NOT FOUND: duquennoy15orchestra as a bootstrapping mechanism for a 6TiSCH network: each node has a “rendezvous” cell in the schedule, the position of which is computed by applying a hash function to its address. Neighbor nodes thereby know at what time and on which frequency it is listening. Can we extend the concept of autonomous cells to support mobility? Since no signaling is needed to set up this cell, nodes can move without communication overhead from re-scheduling. We can for example allow nodes to change the number of autonomous cells it has (adapting for changes in traffic), and communicate that number for example in Enhanced Beacons. We can evaluate this extension of the 6TiSCH standard on the 6TiSCH simulator, and answer the question: what is the speed limit of the micro-robots at which point the network cannot adapt to the resulting topological changes? That speed limit depends on the communication range. Furthermore, we need to look at the overhead associated with a robot losing connectivity to the swarm: how long can it lose connectivity while staying synchronized?How long does it take for it to reconnect?
- Micro-robots exchange data in a peer-to-peer fashion, rather than all sending data to a single collection point as in a sensor network. The first question we want to answer is: does the peer-to-peer mode of an IoT routing protocols such as RPL apply to such a dynamic network? Given our previous work on this protocol the answer is most likely “no”, and we will need to take a new approach. We worked on the concept of “virtual coordinates” CITATION NOT FOUND: watteyne09centroid, some of which we have used to create RPL. The question is: can we re-purpose the concept of virtual coordinates to support peer-to-peer communication in a micro-robotics context? We will extend RPL to have multiple DODAGs: each potential destination is the root of a new DODAG, which it announces by sending RPL DIOs. We then use reinforcement-based learning to maintain only the DODAGs which are actively used.
- The IoT-lab testbed Inria manages includes robots. The Lille deployment contains 64 Turtlebot2 robots. These are large robots approximately 40 cm high, but are an ideal ready-to-use platform for experimentally evaluating the scheduling and routing approaches described above. We will equip these with micro-motes, and verify the performance of the micro-mote-based mesh network as we have the robots move on a hardcoded track. The question we want to answer is: what are the mobility patterns which stress the mobile mesh network the most? There is a trade-off between the mobility algorithm in the swarm which stretches the robots away from one another to progress fast, and the TSCH network which operates best when each robot has many neighbors.
Results: From a scientific point of view, a completely new approach to scheduling and routing in TSCH networks, which are evaluated both in simulation and experimentally on a testbed. These new scheduling and routing protocols are standardized in the 6TiSCH and ROLL IETF working groups. From a project point of view, A2.1 develops the networking stack which is the stepping stone for A3.1 (which adds localization) and the experimental validation.
[A2.2] Wireless Control Loops and Latency Predictability
As we have shown in CITATION NOT FOUND: brunlaguna18smartMesh, implementations of TSCH networks such as Analog Devices' SmartMesh IP guarantee delivery. That is, a TSCH network guarantees that data reaches the destination. The catch is that it does not guarantee when. Given the unreliable nature of wireless, this makes sense: if my neighbor did not get my frame, I retransmit until it does. One can even argue that, given an infinite amount of time and a connected network, only an implementation bug can justify not having 100% reliability. The next question is: can a TSCH network guarantee latency? The answer to that is “no”, since there is always a non-zero probability of an infinite amount of retries to happen on a link that has a packet delivery ratio strictly below 100%. The bold and ambitious question this work package aims to answer is: can TSCH network offer predicable latency and be used to run control loops? We have anecdotally shown in CITATION NOT FOUND: schindler17implementation that the control loop of an inverted pendulum can run through a TSCH network, but without rigorous proof.
This objective leads to the following 3 studies:
- For the latency of a network to be predictable, the easiest is that it does not depend on the amount of traffic in the network. In a TSCH context, this means that the schedule is collision-free. While collision-free schedule is straightforward when using a centralized scheduler, the question is: can we achieve collision free scheduling in a distributed setting such as a swarm of micro-robots? One way of answering is to solve the following mathematical challenge: find a whitening function which turns a small number into a set of cells in a schedule, in such a way that any two different numbers result in disjoint sets of cells. If we can solve this, we can assign a unique number to each node in the network (possibly during secure join), which the whitening function turns in a collision-free schedule.
- Minet et al. CITATION NOT FOUND: minet19optimal have shown on very simple topologies that it is possible to turn a connectivity graph and a schedule into a distribution of latencies, for stable topologies and convergecast traffic. This is similar to the repetition strategy used by 3GPP in the NB-IoT protocol. Can we extend that work to take into account a changing topology, changing schedules and any-to-any traffic? While the approach involves probabilistic analysis, it most likely results in a computational approach. This tool can then be used to explore trade-offs between throughput and power consumption on the one hand, and average latency and latency distribution on the other.
- The two studies above are a necessary mathematical foundation, but can we turn that mathematical foundation into working scheduling approach? Consistency cannot be guaranteed in a practical setting, i.e. nodes do not all have the same information at the same time, which we need to take into account using protocol engineering. To evaluate this protocol, we can define a control loop on the IoT-lab robots, for example a maximum round-trip time between two mobile nodes, and verify that our scheduling approach successfully closes that loop, while we control the movement of the robots.
Results: From a scientific point of view, a whitening function that serves as the cornerstone for a collision-free scheduling algorithm with a predictable latency distribution. This whitening function is formally proven, while the overall scheduling approach is implemented and exercised on different scenarios on the IoT-lab robots. From a project point of view, A2.2 develops the scheduling aspect of the protocol stack which allows micro-robots to communicate with predictable latency.
[A2.3] Agile Networking
Today's low-power wireless devices typically consist of a micro-controller and a radio. The most commonly used radios are IEEE802.15.4 2.4 GHz, IEEE802.15.4g sub-GHz and LoRA (SemTech) compliant. Radios offer a different trade-off between range and data-rate, given some energy budget. To make things more complex, standards such IEEE802.15.4g include different modulations schemes (2-FSK, 4-FSK, O-QPSK, OFDM), further expanding the number of options.
“Agile Networking” is the concept we are developing which redefines a low-power wireless device as having multiple radios, which it can possibly use at the same time. That is, in a TSCH context, for each frame a node sends, it can change the radio it is using, and its setting. If the next hop is close, it sends the frame at a fast data rate, thereby reducing the radio on-time and the energy consumption. If the next hop is far, it uses a slower data rate.
The first challenge was hardware support. With our input, the OpenMote company designed the OpenMote B, which contains both a CC2538 IEEE802.15.4 radio, and an AT86RF215 IEEE802.15.4g radio, offering communication on both 2.4 GHz and sub-GHz frequency bands, 4 modulation schemes, and data rates from 50 kbps to 800 kbps.
The second challenge is to redesign the protocol stack in a standards-compliant way. We are working on a 6TiSCH design in which neighbor discovery happens independently on each radio, and the same neighbor node can appear as many times in the neighbor table as it has radios. The goal is to standardize an “Agile 6TiSCH” profile, without having to touch the core specifications. Jonathan Munoz has co-authored an Internet Draft which details the impact agile networking has on the IETF 6TiSCH protocol stack. This is being implemented in OpenWSN by Mina Rady. The next step is to evaluate the performance of the solution.
3.3 [A3] Security in Constrained Systems
Securing the traditional Internet has been a bumpy ride for the last 30 years, but recently we have witnessed progress, notably with major standardization bodies advocating against pervasive monitoring CITATION NOT FOUND: rfc7258. On the IoT side, however, popular magazines are full of stories of hacked devices (e.g. drone attack on Philips Hue), IoT botnets (e.g. Mirai), and inherent insecurity. A saying in the IETF, the standardization body behind the technical solutions of the Internet, goes: “The S in IoT stands for security.”
Why has the IoT industry failed in adopting the available computer security techniques and best practices? Our experience in the research community, industry, and the standards bodies has shown that the main challenges are:
- The circumvention of the available technical solutions due to their inefficiency.
- The lack of a user interface for configuring the product in the field resulting in default parameters being (re)used.
- Poorly tested and unverified software, often lacking or providing an insecure software upgrade mechanisms.
Our research goal is to contribute to a more secure IoT, by studying and proposing technical solutions to these challenges for low-end IoT devices, with immediate industrial applicability and transfer potential.
[A3.1] Lightweight Protocols and System-level Integration
The last couple of years have witnessed a significant progress in secure communication protocols for the IoT. The IETF has taken steps in standardizing new solutions for protecting the communication channel (e.g. OSCORE, TLS 1.3) and 3-party authorization protocols (e.g. ACE framework). These new solutions have been demonstrated as much more efficient than their predecessors (e.g. TLS 1.2, OAuth 2 as used in the Web), and are expected to be deployed with the next generation of IoT products CITATION NOT FOUND: restuccia20lowpower, CITATION NOT FOUND: gunnarsson21evaluating. There are a couple of remaining pieces to complete the IoT puzzle. One of those pieces is the LAKE protocol – to be standardized by the group we co-chair in the IETF – a lightweight authenticated key exchange protocol for IoT. As an important building block, the LAKE protocol is expected to enable key exchange in the most constrained Internet-of-Things use cases CITATION NOT FOUND: draft-ietf-lake-reqs.
A common assumption for these communication security solutions is that the trust relationship between the different entities involved in the communication has already been established through for example common keying material, root trust certificates. At manufacturing time, the trust relationship is typically established between the IoT device and the manufacturer. However, the domain where the IoT device will be installed is not known at manufacturing time, and before the IoT device can join a given domain, it needs to be provisioned with domain-specific credentials. Bootstrapping this trust relationship between the IoT device and the domain owner is typically considered out-of-scope for the standards bodies, yet it is a non trivial task as IoT devices lack a user interface. Companies typically resort to out-of-band channels (e.g. NFC, ad-hoc wireless network, pre-shared keys printed on the back of a device, serial port) or proximity-based authentication, requiring the user to go through a cumbersome process of installing a new IoT device. This opens up various vulnerabilities as the “bootstrapping” protocol ends up being designed in-house, without a thorough review of the community and security experts.
One challenge is to enable a solution that allows an IoT device to join (mutually authenticate, authorize, be provisioned with parameters) a network in a new administrative domain, with zero pre-configuration of the IoT device required by the user CITATION NOT FOUND: draft-selander-ace-ake-authz. One cornerstone component of such a solution is the LAKE protocol CITATION NOT FOUND: draft-ietf-lake-edhoc. The open research questions include the provisioning of network bandwidth for initial bootstrapping in a zero-touch manner, efficient but flexible transport of public-key certificates.
With LAKE standardization under way, expectations are high in that the working group will provide an efficient key exchange solution for IoT that has been missing. This opens up questions on how the LAKE protocol compares to TLS 1.3 in terms of security and performance, which we plan on answering. Also, in collaboration with the Inria PROSECCO team, we work on a formally verified implementation of the LAKE protocol in the OpenWSN environment, similarly to what has been done during the standardization of TLS 1.3 CITATION NOT FOUND: bhargavan17verified.
Software update mechanisms are being standardized by the IETF CITATION NOT FOUND: draft-ietf-suit-architecture. Their use to patch vulnerabilities is primordial in constrained environments to improve the reputation IoT products have in terms of security. We plan to study these mechanisms CITATION NOT FOUND: zandberg19secure in the context of 6TiSCH networks to improve their performance and make it approachable to product designers.
Results: From a scientific point of view, we plan on delivering a turn-key, open-source solution for network access of constrained devices, which does not require user input at deployment time. We plan on publishing a comparative study focusing on performance in constrained environments between the LAKE protocol and TLS 1.3. We also plan on implementing the software update mechanism in 6TiSCH networks and improving it to support software updates of large networks. The envisioned work includes both the derivation of new algorithms and protocols, as well as the optimization of existing solutions.
[A3.2] Microrobot Swarm Security
We plan on exploring the applicability of security mechanisms developed and standardized as part of A3.1 with the swarms of constrained micro-robots. There are several challenges that we envision on such a path.
Highly dynamic logical topologies: Considering the structure such as a swarm of micro-robots moving through space, the wireless links between them are expected to have time-variant quality. As a consequence, we can expect highly dynamic logical topologies between nodes in the network. In such conditions, where a node constantly discovers and communicates with new neighbors, how do we ensure that adequate pairwise cryptographic keys are in place? This problem is similar to what is encountered in Mobile Ad-hoc Networks (MANETs), but the constraints of SCuM nodes are much higher. Can we use the protocol(s) standardized by the LAKE standardization working group, or channel-anonymity-based solutions CITATION NOT FOUND: sciancalepore19exchange?
Securing Localization: Being able to localize nodes within a swarm is an essential feature from the application standpoint. To that end, as outlined in A4.2, we plan on using an approach with mobile lighthouses CITATION NOT FOUND: kilberg20accurate, each equipped with lasers that periodically sweep the surrounding space. How to protect such a system from (accidental) Denial of Service attacks where the attacker randomly points a laser towards the network?Can we use the fact that mobile lighthouses are equipped with radio transceivers and can communicate with the SCuM nodes? We plan on studying whether lighthouses can use the radio channel to authenticate their broadcasts (e.g. using TESLA-like solutions CITATION NOT FOUND: perrig02tesla) and exchange the supplementary information in order to pseudo-randomly change the sweep pattern, such that the presence of the attacker does not disturb the network's localization feature.
Absence of a stable clock source on SCuM: The fact that SCuM has no external components means that it also has no crystal oscillator to use as a stable clock source. This changes the very basics of how wireless networking is done CITATION NOT FOUND: chang206tisch. The work laid out in in A1.2 aims at using the network of micro-robots to provide a relatively stable clock source to each individual SCuM. Instead of trusting its local clock, the nodes in the IoT network must now additionally use the network-provided information. However, this opens up an attack vector where the attacker can disturb the network by simply heating up some of the nodes and changing their clock drift. We plan on exploring the use of machine learning techniques on network drift patterns in order to design an Intrusion Detection System (IDS) to detect nodes under attack.
Results: This research axis plans on closely following the team developments on micro-robot swarms and ensuring that the appropriate mechanisms are secure-by-design. To that end, the challenges presented serve as an example of the scientific studies we plan on pursuing.
3.4 [A4] Swarm Robotics
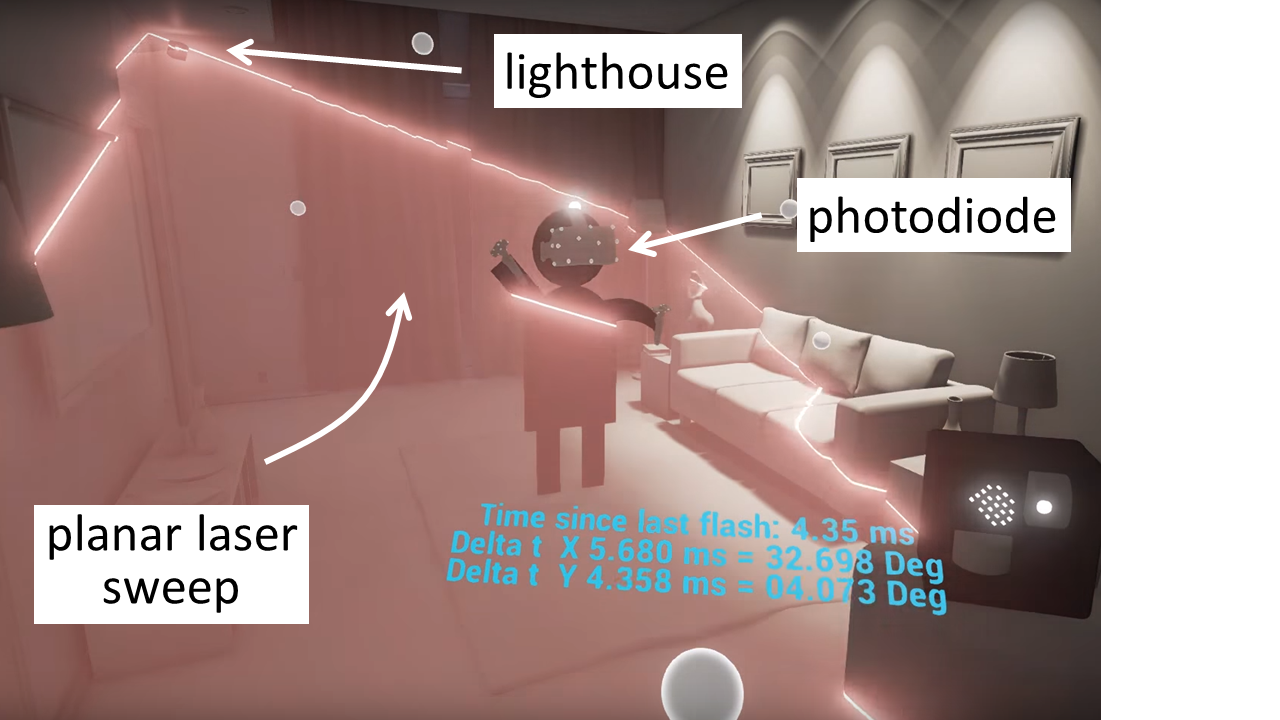
Micro-robots need to know where they are. The constrained nature of these devices, and the lack of any infrastructure makes this a unique problem, to which motion capture systems, or solutions based on resource-heavy sensors do not apply. Can we augment these micro-robots with minimal sensors and smart algorithms which allows them to self-localize using only local measurements? There is very little related work on lighthouse and ultrasonic localization on micro-robots. As shown in Fig. 2, each lighthouse is equipped with lasers that periodically sweep the surrounding space. “All” the mobile device needs to have is a lightsensor to precisely time when laser sweep passes it to find it's location is polar coordinates relative to that lighthouse. We can exploit the fact that the network is synchronized, and we can equip some of the robots with a combination of ultra-sonic transducers, planer lasers and photodiodes. To take the limited accuracy of relative bearing and distance measurements into account, the mathematical tools we have at our disposal include state estimation and sensor fusion, for example through Extended Kalman Filters (EKF). This work will result in a solution for micro-robots to cooperate and discover each robot's location, in real-time, possibly by having a heterogeneous set of specialized robots.
This area of research is further divided into two strands.
[A4.1] Mathematical Framework for Constrained Localization
Localization is key to any robotic application, and many solutions have been developed. Out of those, lighthouse bearing measurement and ultrasonic range measurements are simple enough sensors that they can be integrated in a subset of micro-robots relatively easily. Wheeler et al. CITATION NOT FOUND: wheeler19low have shown that SCuM can detect the laser from a commercial lighthouse. In parallel to a more experimental work, this research area looks at the mathematical framework for constrained localization.
In this work, we assume all robots can be equipped with a lighthouse and/or an ultra-sonic transducer, which allows them to measure relative bearings and distance. The goal is to localize each robot, possibly in a coordinate system which is relative to the swarm. Yet, what is the mathematical framework for turning local bearing and distance measurements into localization, and what is the resulting localization accuracy? We combine mathematical modeling and simulation to answer:
- Assuming all nodes are equipped with a lighthouse, they can measure the relative bearing to one-another. It is well understood that having all relative bearing measurements is enough information to localize all nodes to one another CITATION NOT FOUND: hammel89optimal. The challenge is that, in any practical scenario, each bearing measurement comes with some error, and not all measurements happen at the same time. We first consider a simple case where all micro-robots are within lighthouse range of one another: given the exact position of two “global anchor” micro-robots, how accurate can we get the location of all other robots, and how does that change with having more measurements? This study involves state estimation. We formulate the state estimation model using an Extended Kalman Filter (EKF) to answer the following questions: How many bearing measurements do I need to have a localization measurement better than X mm?How does the inaccuracy of the bearing measurement impact the location? We introduce this mathematical model in a simulation with robots far enough from each other than they form a “multi-hop” topology rooted in these two global anchors.
- We add local distance measurements from ultrasonic transducers to our model, and use our EKF for sensor fusion. This allows us to answer the following question: how much more accurate is the localization if we combine bearing with distance measurements, compared to bearing alone, or distance alone? This helps us navigate the cost/accuracy trade-off, and compare our EKF-based methodology with well-established literature on localization using ultra-sonic measurements CITATION NOT FOUND: navarroserment99beacon, CITATION NOT FOUND: grabowski00heterogeneous.
- Robots move, which limits the number of bearing measurements for each location. By introducing movement in the simulator, we can answer the following questions: what is the mobility pattern (maximum velocity, pause period, etc.) which yields an appropriate trade-off between speed of progression of the swarm and localization accuracy?
- It is unnecessary to equip each robot with a lighthouse (the laser transmitter); a heterogeneous swarm is possible, in which a portion of robots are equipped with a laser transmitter, the others with only a photodiode. The question becomes: what is the trade-off between the portion of laser-equipped robots and localization accuracy?
Results: From a scientific point of view, A4.1 creates the mathematical framework for a localization solution which combines lighthouse and ultrasonic range measurements, in an infrastructure-free, distributed and mobile context. A state estimation and sensor fusion approach allows us to explore trade-offs between accuracy and cost, and understand the impact of robot movement, and of the portion of lighthouse robots on localization accuracy. From a project point of view, A4.1 allows us to decide what hardware to build for experimentation. The model we develop in A4.1 is used as-is in A4.2.
[A4.2] Localization and Network Stack Co-Design
The goal of A4.2 is to co-design the localization solution (the model is built in A4.1) and the networking stack. There are two aspects to this. On the one hand, the network puts constraints on the localization system, in particular on the amount of data that can be exchanged per period of time, and the associated latency. On the other hand, the synchronized and scheduled nature of the networking stack presents a tremendous opportunity for the localization solution: coordinating when the different sensors are on, yielding a better coexistence and power savings. Similar system-level studies can be found CITATION NOT FOUND: nemsick17cooperative, CITATION NOT FOUND: navarroserment99beacon, CITATION NOT FOUND: grabowski00heterogeneous, yet none to be best of our knowledge focuses on extremely constrained micro-robots. The system-level questions we want to answer is: What is the overhead of localization on the network?How scalable is a lighthouse and ultrasound-based localization?How low-power can a mote participating in the network and the localization be? We use simulation and modeling.
- For a lighthouse, using the laser consumes power, and makes it harder for another lighthouse to also have its laser on. The same holds for the ultra-sonic transducers. Can we use the synchronized nature of the network to schedule when each lasers and ultrasonic transducers are on, in such a way that only one pair of close nodes measures their relative bearing and distance at any given time? The scheduled nature of these measurements has two immediate advantages. First, the swarm scales to more robots, as a collision-free localization schedule can be injected. Second, the robots switch their lighthouse and ultrasound only exactly when they know they will be ranging, resulting in ultra-low power operation, key for immobile robots that want to extend their battery lifetime.
- Each node knows a relative bearing and distance to each or its neighbors. Can this information be shared in such a way that all nodes can compute their location? This location can be computed in a coordinate system that is local to the swarm. The goal of this task is to extend the 6TiSCH protocols with a mechanism to share local measurements, and a distributed localization algorithm.
- The protocol resulting from the previous task necessarily comes with some latency, which results in inconsistency between the view of that information. What is the impact of this inconsistency on location accuracy?
Each of these studies results in a new algorithm or protocol, which is first analyzed then evaluated through simulation.
Results: From a scientific point of view, this research has the potential of deeply changing indoor localization as it develops a full RTLS using micro-robots with extreme constraints, in particular in a heterogeneous setup. The result is a method by which a swarm of micro-robots localizes as it progresses through some space. From a project point of view, A4.2 is the last building block to realize the exploration and mapping expedition, including experimentally.
[A4.3] Coordination & Control of a Robotic Swarm
Two important considerations when programming large numbers of tiny cyber-physical agents is: what is the easiest way to program them, either individually, or en masse, and, perhaps more importantly, how can a programmer debug them? When the platforms themselves are on the mm or cm scale, the mass and volume requirements to make physical contact are prohibitive. The fact that the robots could move during live programming or debugging.
Four different approaches to contact-free programming will be compared for various swarm robotic applications. The first two are optical: both focused optical communication, and large-scale optical communication. The second two are electromagnetic: near-field communication (NFC) and far-field communication over a wireless data link. All of these have been used in the past to program cyber-physical systems, but we propose to perform a comprehensive survey on their reliability (effectively, program error rate). Furthermore, there is little effort on how these communication systems can be used for debugging, along the lines of a wireless JTAG interface. And, most importantly, we propose to study how these communication interfaces scale in performance with severe volume limitations. As an example, received optical power scales linearly with diode area, assuming uniform illumination.
For contact-free debugging, the problem is less constrained, as it is difficult to quantify how “easy” a system is to work with. Because physical access is impossible, not all on-board voltages and logic levels are accessible. But, it is feasible to create a back-and-forth communication between the robot's on-board processor and the programmer where certain logic levels and registers can be observed remotely, aiming for a wireless JTAG. This may not be realistic in the en-masse optical programming, although these robots could use diagnostic LEDs that can be read by the user (at low data-rate). The point-to-point laser programmer can also receive data from an on-board LED. The far-field RF communication presumably has a link already established, so debugging can be performed over any communication standard that the robot normally uses (earlier examples of Bluetooth or IEEE 802.15.4 are both valid). The near-field programming could be modified to incorporate an RFID style backscattering to send data from the device to the programmer.
Metrics, like power consumption, programming time, reliability (program error rate) and debug latency will all be concretely measured and compared. User safety, particularly in the case of IR programming for point-to-point optical, or heating due to the potentially low efficiency of near-field capacitive or inductive programming, will also be considered. A more holistic survey of experienced embedded systems engineers will also be performed to determine which programming strategy is most desirable, from the user's perspective, in various applications (single robot, two robot, and many robot, with either a uniform code-base, or a diverse and heterogeneous code-base).
3.5 [A5] Vehicle Area Networking
Vehicle Area Networking (VANETs) have been a research focus of the team, in particular broadcasting and opportunistic routing schemes. The AIO team continues working on these subjects, while extending them to medium access schemes. We also consider higher level transmission scenarios. For instance, the team plans to study how safety messages can be used to assist the driver, possibly by performing automatic maneuvers in VANETs.
[A5.1] Improvement of communications protocols
The standard IEEE 802.11p protocol has been shown no to scale properly the density of vehicles rapidly varies. In EVA, we have proposed enhancement of the IEEE 802.11p access scheme by considering an adaptive carrier sense level CITATION NOT FOUND: bouchaala15analysis, CITATION NOT FOUND: achir16optimisation. The idea is to create local communication and to allow the network traffic to scale with the density of the vehicle. Detailed proposals have been developed during Younes Bouchaala thesis CITATION NOT FOUND: bouchaala17gestion. Another approach is to use a TDMA approach. The main concept is to use the position of vehicles on the roads to control the slots allocations CITATION NOT FOUND: hadded16infrastructure, CITATION NOT FOUND: hadded18tdma. This technique allows to drastically reduce packets collision. We can use a decentralized (possibly using cluster heads) or a centralized approach assisted by roadside units CITATION NOT FOUND: hadded16centralized. These studies have been carried during Mohamed Hadded thesis CITATION NOT FOUND: hadded16design. We are currently working to improve these approaches. The idea is to use active signaling techniques in combination with TDMA approaches CITATION NOT FOUND: boukhalfa19active. The active signaling techniques work as an advanced CSMA scheme and thus bring to the protocol the advantage of random access scheme. We can thus benefit from the stability of the TDMA approaches whereas the active signaling scheme allows the protocol to reduce the collision and offer low latency access when required CITATION NOT FOUND: boukhalfa20performance, CITATION NOT FOUND: boukhalfa20physical, CITATION NOT FOUND: boukhalfa20coexistence. This present work will Fouzi's Boukhalfa thesis whose defense is scheduled in October 2021. We can probably even improve your protocol if we use another communication medium such as the visible light. We have started to propose a new architecture which uses simultaneously visible light and radio communication. The smart combination of these two media will be on the focus of our work during the next research period.
We have to study if the visible light communication is mature enough to be used in VANETs in replacement of radio links. The question of the performance and the stability of the visible link is not satisfactorily answered. According to the present state of the art vlc, there are significant problems with interference (natural light, car headlight) CITATION NOT FOUND: khoder20impact, and beam propagation due to vehicles trajectories and their movements. Thus vlc appears more to be a complementary technology to radio communication than a technology that can be used alone. So we do not know yet if the visible light links can be used reliably or if we can use them only as backup liaison to increase our protocols reliability .
The standard IEEE 802.11p protocol has slowly started its deployment in the real life leaving the door open to operator initiative. 5G has developed an approach for vehicles promising a very low latency access for vehicles. We need to better understand what are the 5G services for vehicular networks and what are their strength and limitations We plan a collaboration with the RITS team to deploy a 5G vehicular network in Rocquencourt. More specifically we plan to use 5G network to send Cooperative Awareness Messages CAMs and Decentralized Emergency Notification Messages and to develop a 5G assisted intersection crossing application. We will try to take benefit of this deployment to evaluate how 5G could scale on a real VANET network.
[A5.2] Towards Autonomous Cars
Autonomous driving is a target followed by many new companies such as Google, Uber, Telsa, and even by older players in the field such BMW, Mercedes, etc. Recent progress has been accomplished but it is still unclear whether whether full autonomous vehicles can be obtained in large amount of different cases or if we have to treat only special case such as driving in platoon. The exact role of communication in an autonomous car also remains to be further studied even the importance of the vehicular communication networks has been acknowledge CITATION NOT FOUND: maalej18vanets, CITATION NOT FOUND: wadea17enhancing.
We wish to start by the study of platoons of vehicle and to design the suitable communication network to ensure a high degree of safety. The idea is to use the concepts of CITATION NOT FOUND: lelann19cyberphysical and to adapt them to the protocol AS-DTMAC that we have recently designed. Given the nature and the probability of hazards and assumptions on packet transmission errors, we plan to compute the probability that our platoon of vehicles communicating with our protocol, and according to strict rules, can safely progress. The use of VANETs can be studied in other simple situation such as keeping safe distance between vehicles, changing lanes or inserting in a lane at the entrance of an highway. We plan to combine the use of radio VANETs with other sensing technologies (RADAR, LIDAR, Video) or even with visible light communication to increase the reliability of the system. We believe that as any safety system, autonomous cars have to rely on many different and independent sensing systems to be able to ensure a high degree of reliability. We will have to
We also have to study if the visible light communication is mature enough to be used in VANETs. According to the present state of the art vlc, there are significant problems with interference (natural light, car headlight) and beam propagation due to vehicle trajectories and their movements. Thus vlc appears more to be a complementary technology to radio communication than a technology that can be used alone.
[A5.3] Machine learning and VANETs
Vehicular networks can generate a lot of data; the vehicles have positioning capabilities (e.g. GPS), they also have communication devices and computing power. We have shown that the power received from packets transmitted by road side units can be used by machine learning algorithms such as Random Forest (RF) , K Nearer Neighbors (KNN), Neural Networks (NN) to predict the position of the vehicle and performance of the wireless network (e.g. packet delivery ratio) see CITATION NOT FOUND: sangare18predicting, CITATION NOT FOUND: sangare18transmission, CITATION NOT FOUND: sangare19comparing. We have shown that these prediction can obtained even a significant portion of the measurements are lost and that the predictions still remain exploitable. We believe that these results remain to be improved, for instance the use communication data with input of other sensor appear to be very promising. These studies will depend on the availability of large amount of vehicle network data.
It is also possible to use machine learning to forecast accidents. Urban traffic forecasting models generally follow either a Gaussian Mixture Model (GMM) or a Support Vector Classifier (SVC) to estimate the features of potential road accidents. Although SVC can provide good performances with less data than GMM, it incurs a higher computational cost. We have proposed framework that combines the descriptive strength of the Gaussian Mixture Model with the high-performance classification capabilities of the Support Vector Classifier. A new approach is presented that uses the mean vectors obtained from the GMM model as input to the SVC. Experimental results show that the approach compares very favorably with baseline statistical methods, see CITATION NOT FOUND: sangare20exploring. Advances are possible in forecasting accidents, these progresses depend on the availability of data, in particular covering a wide variety of problems from simple incidents to accidents with injuries to fatalities. It is clear that such a system could be very interesting for a driver who could in dangerous conditions increase his attention and even activate driving aids.
The positioning of the AIO team in machine learning for VANETs consists of using and combining techniques already available and exploiting these techniques in open data sets. This positioning is different from that of the SIERRA team which seeks the design of a new algorithm preferably to solve fundamental problems in networks. For example in AIO we plan to use a customized Deep Learning mechanism-based congestion control identification approach that does not need any enriched domain knowledge other than training traffic of a congestion control variant. By only using packet arrival data, it is also directly applicable to encrypted (transport header) traffic. At the same time, during the customization phase, we will also use deep reinforcement learning to consolidate the congestion control. Trust Region Policy Optimization (TRPO) and proximal policy optimization will be adopted in the proposed customized approach as the measure of optimization.
[A5.4] Security and Privacy in VANETs
Security in VANETs has already been the subject of numerous studies CITATION NOT FOUND: hasrouny17vanet, CITATION NOT FOUND: manivannan20secure. Attacks can be carried out in several places: on the air interface of the network, in the hardware or software of vehicle transmissions, in the vehicle sensors whose information is sent over the network, in the infrastructure of the VANET network. All types of security attacks can be found in vehicular networks and the dynamics of network links add further complexity to the problem. Faced with the difficulty of the problem, VANET networks still have an advantage, the vehicles and infrastructure elements have significant computing power and energy resources. The classic security approach in VANETs is the deployment of a PKI. This approach has been standardized in Europe at ETSI and in the US. This approach does not solve all the issues and gives rise to problems in particular of Privacy. To remedy this, the technique of pseudonyms has been proposed CITATION NOT FOUND: adigun13protocol.
The approach of the AIR project is not to study security in VANETs networks in general but to propose punctual improvements of the state-of-the-art on precise and well-defined security problems.
VLC links could be used between vehicles for communications. We plan to study how the use of such a link could advance security in VANETs. With the nature of VLC links, it is clear that capturing messages or sending of fraudulent packets is almost impossible in the context of point to point VLC links. On the privacy side, the use of VLC links can be very beneficial. We plan to quantify this benefit compared to existing solutions.
Another area we want to tackle is the security of routing protocols in VANETs. We have started to study security attacks on cross-layer routing and the benefit of trust against these attacks CITATION NOT FOUND: baccari20performance, CITATION NOT FOUND: baccari20secure. Ismael Tayssir in her PhD plans to development of a new intelligent routing protocol which uses information from the MAC layer to find an optimized path between the transmitter and the receiver and which takes into account the specificities of the transmission medium while minimizing the time of transmission. In her PhD, detection of malicious behavior at the MAC and routing layer will be proposed to secure the routing protocol developed.
We also have started very preliminary studies to use blockchains in VANETs CITATION NOT FOUND: sangare20graph. We will continue on this topic and will try to determine if there are cases of applications in VANETs where this technology can find its best application.
The RITS team works primarily on security issues in VANETs caused by the sending of fraudulent or erroneous data coming from vehicle sensors. Collaboration between our team and RITS in this area is possible.
4 Application domains
4.1 Industrial Process Automation
Wireless networks are ubiquitous and are an integral part of our daily lives. These networks are present in many application domains; the most important are detailed in this section.
Networks in industrial process automation typically perform monitoring and control tasks. Wired industrial communication networks, such as HART, have been around for decades and, being wired, are highly reliable. Network administrators tempted to “go wireless” expect the same reliability. Reliable process automation networks – especially when used for control – often impose stringent latency requirements. Deterministic wireless networks can be used in critical systems such as control loops, however, the unreliable nature of the wireless medium, coupled with their large scale and “ad-hoc” nature raise some of the most important challenges for low-power wireless research over the next 5-10 years.
Through the involvement of team members in standardization activities, protocols and techniques are proposed for the standardization process with a view to becoming the de-facto standard for wireless industrial process automation. Besides producing top-level research publications and standardization activities, this activity fosters further collaborations with industrial partners.
4.2 Environmental Monitoring
Today, outdoor IoT networds are used to monitor vast rural or semi-rural areas and may be used to detect fires. Another example is detecting fires in outdoor fuel depots, where the delivery of alarm messages to a monitoring station in an upper-bounded time is of prime importance. Other applications consist in monitoring the snow-melt process in mountains, tracking the quality of water in cities, registering the height of water in pipes to foresee flooding, etc. These applications lead to a vast number of technical issues: deployment strategies to ensure suitable coverage and good network connectivity, energy efficiency, reliability and latency, etc.
We work on such applications through associate team “SWARM” with the Pister team at UC Berkeley.
4.3 The Internet of Things
The Internet of Things (IoT) is composed of small, often battery-powered objects that measure and interact with the physical world, and encompasses smart home applications, wearables, smart city and smart plant applications.
It is essential to (1) clearly understand the limits and capabilities of the IoT, and (2) develop technologies which enable user expectation to be met.
The AIO team is dedicated to understanding and contributing to the IoT. In particular, the team maintains a good understanding of the different technologies at play (Bluetooth, IEEE 802.15.4, WiFi, cellular), and their trade-offs. Through scientific publications and other contributions, AIO helps establish which technology best fits which application.
4.4 Military, Energy and Aerospace
EVA has developed cutting-edge expertise in using wireless networks for military, energy and aerospace applications. Wireless networks are a key enabling technology in these application domains, as they allow physical processes to be instrumented (e.g. the structural health of an airplane) at a granularity not achievable by its wired counterpart. Using wireless technology in these domains does however raise many technical challenges, including end-to-end latency, energy-efficiency, reliability and Quality of Service (QoS). Mobility is often an additional constraint in energy and military applications. Achieving scalability is of paramount importance for tactical military networks, and, albeit to a lesser degree, for power plants. AIO works in this domain.
Smart cities share the constraint of mobility (both pedestrian and vehicular) with tactical military networks. Vehicular Ad-hoc NETworks (VANETs) will play an important role in the development of smarter cities.
The coexistence of different networks operating in the same radio spectrum can cause interference that should be avoided. Cognitive radio provides secondary users with the frequency channels that are temporarily unused (or unassigned) by primary users. Such opportunistic behavior can also be applied to urban wireless sensor networks. Smart cities raise the problem of transmitting, gathering, processing and storing big data. Another issue is to provide the right information at the place where it is most needed.
4.5 Emergency Applications
In an “emergency” application, heterogeneous nodes of a wireless network cooperate to recover from a disruptive event in a timely fashion, thereby possibly saving human lives. These wireless networks can be rapidly deployed and are useful to assess damage and take initial decisions. Their primary goal is to maintain connectivity with the humans or mobile robots (possibly in a hostile environment) in charge of network deployment. The deployment should ensure the coverage of particular points or areas of interest.
The wireless network has to cope with pedestrian mobility and robot/vehicle mobility. The environment, initially unknown, is progressively discovered and may contain numerous obstacles that should be avoided. The nodes of the wireless network are usually battery-powered. Since they are placed by a robot or a human, their weight is very limited. The protocols supported by these nodes should be energy-efficient to maximize network lifetime. In such a challenging environment, sensor nodes should be replaced before their batteries are depleted. It is therefore important to be able to accurately determine the battery lifetime of these nodes, enabling predictive maintenance.
4.6 Types of Wireless Networks
The AIO team distinguishes between opportunistic communication (which takes advantage of a favorable state) and collaborative communication (several entities collaborate to reach a common objective). Furthermore, determinism can be required to schedule medium access and node activity, and to predict energy consumption.
In the AIO project, we propose self-adaptive wireless networks whose evolution is based on:
- optimization to minimize a single or multiple objective functions under some constraints (e.g. interference, or energy consumption in the routing process).
- machine learning to be able to predict a future state based on past states (e.g. link quality in a wireless sensor network) and to identify tendencies.
The types of wireless networks encountered in the application domains can be classified in the following categories.
4.7 Wireless Sensor and Mesh Networks
Standardization activities at the IETF have defined an “upper stack” allowing low-power mesh networks to seamlessly integrate into the Internet (6LoWPAN), form multi-hop topologies (RPL), and interact with other devices like regular web servers (CoAP).
Major research challenges in sensor networks are mostly related to (predictable) power conservation and efficient multi-hop routing. Applications such as monitoring of mobile targets, and the generalization of smart phone devices and wearables, have introduced the need for WSN communication protocols to cope with node mobility and intermittent connectivity.
Extending WSN technology to new application spaces (e.g. security, sports, hostile environments) could also assist communication by seamless exchanges of information between individuals, between individuals and machines, or between machines, leading to the Internet of Things.
4.8 Deterministic Low-Power Networks
Wired sensor networks have been used for decades to automate production processes in industrial applications, through standards such as HART. Because of the unreliable nature of the wireless medium, a wireless version of such industrial networks was long considered infeasible.
In 2016, the publication of the IEEE 802.15.4e standard triggered a revolutionary trend in low-power mesh networking: merging the performance of industrial networks, with the ease-of-integration of IP-enabled networks. This integration process was spearheaded by the IETF 6TiSCH working group, co-chaired by AIO. A 6TiSCH network implements the IEEE 802.15.4e TSCH protocol, as well as IETF standards such as 6LoWPAN, RPL and CoAP. A 6TiSCH network is synchronized, and a communication schedule orchestrates all communication in the network. Deployments of pre-6TiSCH networks have shown that they can achieve over 99.999% end-to-end reliability, and a decade of battery lifetime.
The communication schedule of a 6TiSCH network can be built and maintained using a centralized, distributed, or hybrid scheduling approach. While the mechanisms for managing that schedule are standardized by the IETF, which scheduling approach to use, and the associated limits in terms of reliability, throughput and power consumption remain entirely open research questions. Contributing to answering these questions is an important research direction for the AIO team.
4.9 MANETs and VANETs
In contrast to routing, other domains in Mobile Ad-hoc NETworks (MANETs) such as medium access, multi-carrier transmission, quality of service, and quality of experience have received less attention. The establishment of research contracts for AIO in the field of MANETs is expected to remain substantial. MANETs will remain a key application domain for EVA with users such as the military, firefighters, emergency services and NGOs.
Vehicular Ad hoc Networks (VANETs) are arguably one of the most promising applications for MANETs. These networks primarily aim at improving road safety. Radio spectrum has been ring-fenced for VANETs worldwide, especially for safety applications. International standardization bodies are working on building efficient standards to govern vehicle-to-vehicle or vehicle-to-infrastructure communication.
4.10 Cellular and Device-to-Device Networks
We propose to initially focus this activity on spectrum sensing. For efficient spectrum sensing, the first step is to discover the links (sub-carriers) on which nodes may initiate communications. In Device-to-Device (D2D) networks, one difficulty is scalability.
For link sensing, we study and design new random access schemes for D2D networks, starting from active signaling. This assumes the availability of a control channel devoted to D2D neighbor discovery. It is therefore naturally coupled with cognitive radio algorithms (allocating such resources): coordination of link discovery through eNode-B information exchanges can yield further spectrum usage optimization.
5 Social and environmental responsibility
We are accutely aware of the role Inria and our team plats in society and on the environment. While we are of course primarily focused on our purely scientific duties, we are actively trying to stay connected to society and to be aware of the environment.
As researchers, we have a fantastic tool at our disposal to make a deep change into society: education. We teach classes and short courses mainly to the engineering student and believe that embedded systems are the perfect teaching tool. They offer infinite opportunities to let student “see for themselves”. And adding connectivity to them (low-power wireless for example) allows the students to build very complex chains of information. In the most complete case, information goes from a physical sensor to a micro-controller, through a low-power wireless mesh network, to a gateway, to a single-board computer, to a cloud-based back-end system, to a database, and to the student's browser. Being able to build up this entire chain fast and with relatively simple components is both incredibly motivating for the students (“The dial is moving on my phone!”, “I can control my fan remotely!”), and offers the instructor infinite possibilities to dig into any topic, from SPI buses to RTOS priority inversion, embedded protocols or web interaction. Given that perspective, our first guiding principle when teaching is to “build real things“.
One of the things we see when interviewing people is that students are often not exposed to the technology being used in real-world applications. They have often some experience with open-source projects, development boards and DYI hardware. And while these tools are perfectly valid, they don't convey to the student a clear picture of what the state of the art is. Given that perspective, our second guiding principle when teaching is to use technology that's really out there.
In 2022, we started developing two distinct platforms which can both he used for our research, as well as for education.
The first is the DotBot (www.dotbots.org), an open-source robotic platform. It consists of a printed circuit board and two motors installed on a laser-cut wooden chassis, also featuring an HTC VIVE lighthouse receiver for mm-accurate positions at 100 Hz. The DotBot's wireless System-on-Chip (SoC) allows different DotBots to communicate. We are building a 1,000 DotBot swarm for our research of swarm orchestration. As an open-source platform, DotBot is being designed for education and research well beyond the project. We envision educational and research kits targeting students at the primary school, high school and university levels, with a particular focus on female students. DotBot is a fantastic stepping stone for the community to embrace swarm communication, train the next generation of collaborative node experts and educate students, thereby training the next generation of smart system which incorporate decentralized orchestration, constrained AI and swarm programming.
The second is the AIOT Systems (www.aiotsystems.org), a one-stop shop for learning embedded low-power wireless. The AIOT Play board is a ready-to-learn-on platform, designed specifically to be both easy to learn with, and close to an production system. It features a prototyping area allowing a student to build little circuits directly on the board. They then write firmware directly on the fully programmable micro-controller to interact with the circuit, and hand the data to the true mesh networking module. The source code consists of Python code that runs on a computer, and C code that runs on a micro-controller. The source code is developed under an open-source license so students can really see how things are working, and use it beyond learning. We crafted the AIOT Systems Academy so it is a completely self-contained set of course material. The AIOT Systems Academy is a collection of dozens of short labs. For instructors, the material is ready to present.
Of course, there is no way we can argue the core technology we develop is good for the environment. Any electronic circuit is build from materials and through fabrication method which are harmful. Yet, unlike a cell phones or a tablet, we look for applications in which our sensors are used to prevent events which would have a very negative effect on the environment, and for which the environment cost of the technology is much smaller than the environmental benefit they allow. This is the reason why a lot of our applications are related to the environment. We have deployed sensors to detect early stage of wildfires to be able to put them out before they destroy entire ecosystems (see France 3 interview). We have deployed sensors in marinas to detect fires on board ships, and prevent boats from overconsuming electricity (through our Falco startup). We are working with architects in tropical climates to monitor their buildings to be able to reduce the use of air conditioning (through our collaboration with ESIROI). Besides these projects, we have deployed sensors to detect frost events in vineyards or in peach orchards, combat the invasion of the Asian Hornet that is several impacting an already fragile bee population, or monitoring the snowmelt process in regions prone to draughts. Through this focus on environmental responsibility, we are convinced that the technology we develop has an overall positive impact on our planet.
6 Highlights of the year
6.1 What a Year!
This is the first year of the AIO team. While AIO inherits a lot from the previous EVA team, its research program takes up a new dimension by embracing much more hardware and electronics, and using swarm robotics around which a lot of the research is build: hardware, localization, networking, security. This year was somewhat of a test to see whether we hadn't bitten off too much. Clearly, that was not the case and 2022 was a spectacular year in many aspects.
We started the year with our spin-off startup company, Falco, receiving the IoT Award of the Embedded Trophy run by the French Ministry of Economy. This was a good indication the technology the team has been generating (and which is licensed by Falco) is appretiate by the embedded community, including the big industrial players.
One of the investement with the longest returns in the team leading the Horizon Europe OpenSwarm proposal, and getting it accepted. The 40-month project starts 1-Jan-2023, and brings together the ideal set of partners to push a research agenda which matches pretty much perfectly the research program of the team. Getting OpenSwarm accepted is also, for our team, some sort of validation of the proposed research. We are convinced that OpenSwarm, mainly through the fantastic consortium it brings together, will serve as a fantastic accelerator for our research n 2023 and beyond.
6.2 Awards
- Thomas Watteyne crossed 10,000 citations of his papers, according to Google Scholar
- Thomas Watteyne in the top 2% researcher across all fields, top 0.6% in the “Networking & Telecommunications” field per Stanford’s Prof. Ioannidis work “A Standardized Citation Metrics Author Database Annotated for Scientific Field”.
- Wattson Elements recipient of the IoT Award of the Embedded Trophy (“Trophés de l'Embarqué, catégorie “IoT Grand Public”) on 14-Jan-2022, an annual innovation competition organized in partnership with the French Ministry of Economy, for their Falco product and the innovation roadmap driven by Thomas Watteyne .
7 New software and platforms
7.1 New software
7.1.1 edhoc-rs
-
Name:
EDHOC Implementation in Rust / hacspec
-
Keywords:
Cybersecurity, Internet of things, EDHOC
-
Functional Description:
EDHOC is a lightweight authenticated key exchange protocol targeting constrained environments and Internet of Things use cases. This is a Rust / hacspec implementation of the protocol, adapted for use on microcontrollers.
- URL:
-
Contact:
Malisa Vucinic
7.2 New platforms
7.2.1 DotBot
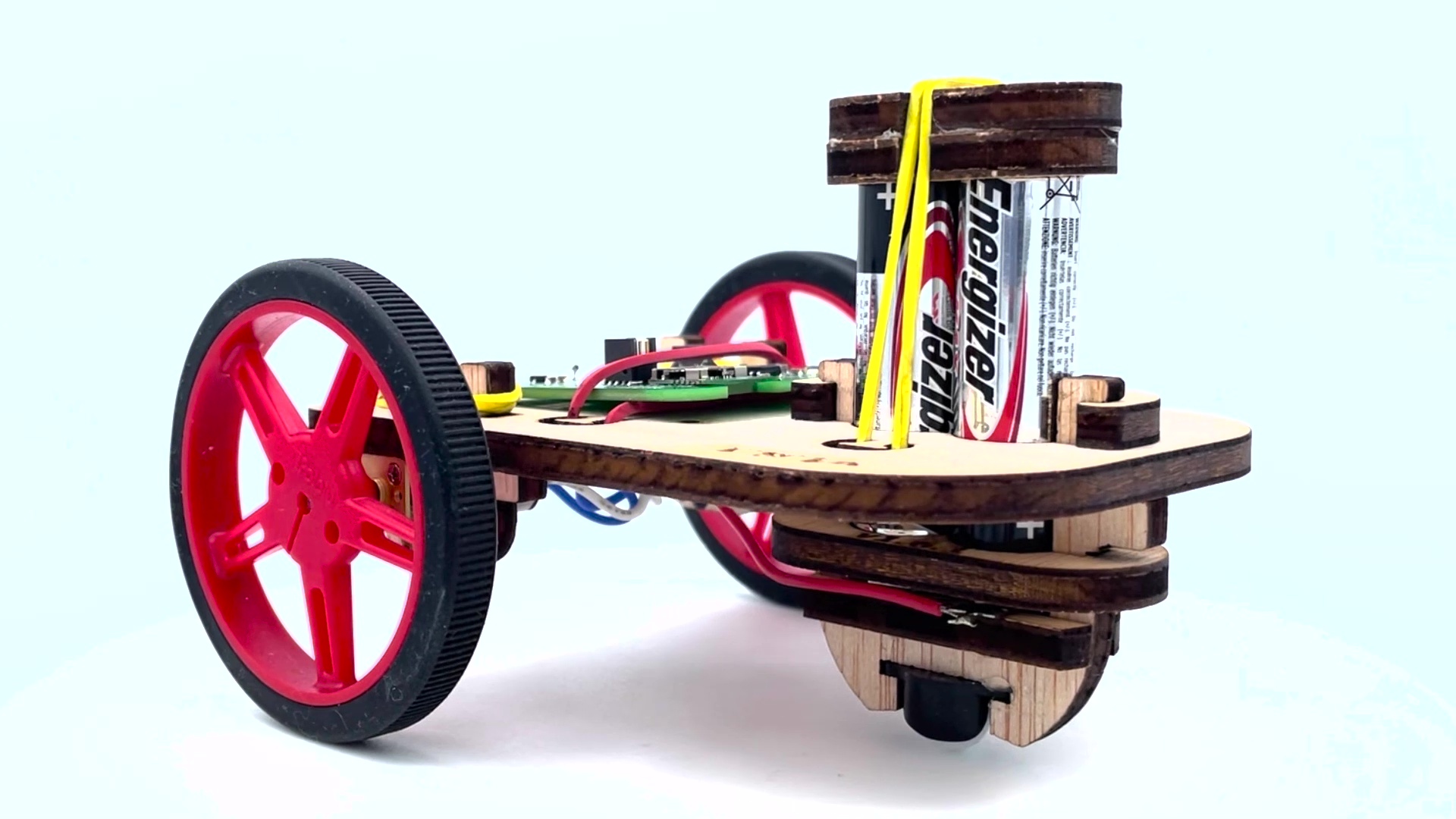
The DotBot swarm robot.
Large, coordinated “swarms” of small, resource constrained robots have the potential to complete complex tasks that single monolithic robots cannot. However, while there is ongoing research, little progress has been made in successfully deploying these swarms in the real world. To help further the field, we are building a research platform called DotBot, show in Fig. 3: a low-price, versatile laser cut robot that can inexpensively act as an agent in a swarm of robots. Each DotBot has two small motors for mobility, accurate localization using laser lighthouses, and can communicate using off-the-shelf radios in either time-synchronized channel-hopping mesh networks originally designed for reliable transmission in crowded IoT networks, or with BLE so that the robots can be programmed from a cell phone or other Bluetooth-enabled device. We see the DotBot platform as an ideal tool for introducing robotics and embedded programming in education. We target three levels. First, in primary school, DotBot serves as a basic introduction to robotics, using simple interaction and remote-control scenarios. In high school, DotBot is used as an introduction to embedded programming, with a focus on the interaction with the real world. Finally, in university, a DotBot swarm is used to introduce the concepts of distributed algorithms, task assignment as well as planning and scheduling.
We have been working hard on the DotBot in 2022. We started the year with a proof-of-concept design which could drive around, but could not self-localize. The work on hardware by Said Alvarado-Marin , on localization by Filip Maksimovic and on algorithms by Razanne Abu Aisheh has allows Alexandre Abadie to “put it all together”. We now have small swarms of handful of DotBots moving around in the lab, self-locazing using the lighthouse. The DotBot features front and center in the Horizon Europe OpenSwarm project. This project, in particular through the very large partners it brings, will serve as a catalyst that will turn our small-scale testbed into a 1,000 DotBot in the next 18 months.
More information at www.dotbots.org.
7.2.2 AIOT Systems
The AIOT Play board.
AIOT Systems is a one-stop shop for learning embedded low-power wireless. The AIOT Play board, shown in Fig. 4, is a ready-to-learn-on platform, designed specifically to be both easy to learn with, and close to an production system. It features a prototyping area allowing a student to build little circuits directly on the board. They then write firmware directly on the fully programmable micro-controller to interact with the circuit, and hand the data to the true mesh networking module. The source code consists of Python code that runs on a computer, and C code that runs on a micro-controller. The source code is developed under an open-source license so students can really see how things are working, and use it beyond learning. We crafted the AIOT Systems Academy so it is a completely self-contained set of course material. The AIOT Systems Academy is a collection of dozens of short labs. For instructors, the material is ready to present.
More information at www.aiotsystems.org.
8 New results
The team's research program, summarized in Section 3, is organized around five axes. We present the results of 2022 following the same organization.
8.1 Related to [A1] Smart Dust
We make some strong leaps in our “Smart Dust” research strand, thanks to very strong collaboration with the UC Berkeley team of Prof. Pister, a collboration which benefits hugely from the SWARM associate team which is in place. The SCuM chip we have been using is very interesting; it can “speak” both IEEE802.15.4 and Bluetooth without needing a crystal. That is, a device can be the size of a grain of rice, which opens up lots of potential applications. We have made a lot of progress in the calibration of the oscillators in that chip, to the point where we are now able to create small multi-hop mesh networks with SCuM chips.
8.1.1 A Temperature-Compensated BLE Beacon and 802.15.4-to-BLE Translator on a Crystal-Free Mote
Participants:

