2024Activity reportProject-TeamFUN
RNSR: 201221009N- Research center Inria Centre at the University of Lille
- Team name: self-organizing Future Ubiquitous Network
- Domain:Networks, Systems and Services, Distributed Computing
- Theme:Networks and Telecommunications
Keywords
Computer Science and Digital Science
- A1.2.1. Dynamic reconfiguration
- A1.2.3. Routing
- A1.2.5. Internet of things
- A1.2.6. Sensor networks
- A1.2.8. Network security
- A1.4. Ubiquitous Systems
- A1.6. Green Computing
- A5.10.6. Swarm robotics
Other Research Topics and Application Domains
- B3.5. Agronomy
- B3.6. Ecology
- B5.1. Factory of the future
- B5.9. Industrial maintenance
- B6.4. Internet of things
- B7.2.2. Smart road
- B8.1. Smart building/home
- B8.1.2. Sensor networks for smart buildings
- B8.2. Connected city
1 Team members, visitors, external collaborators
Research Scientists
- Nathalie Mitton [Team leader, INRIA, Senior Researcher, HDR]
- Valeria Loscri [INRIA, Senior Researcher, HDR]
Post-Doctoral Fellows
- Adriana Arteaga Arce [INRIA, Post-Doctoral Fellow, until Oct 2024]
- Carol Habib [INRIA, Post-Doctoral Fellow]
- Aya Moheddine [INRIA, Post-Doctoral Fellow]
- Amira Mourad [INRIA, Post-Doctoral Fellow, from Jun 2024]
- Damien Wohwe Sambo [INRIA, Post-Doctoral Fellow, until Feb 2024]
- Selma Yahia [INRIA, Post-Doctoral Fellow]
PhD Students
- Ildi Alla [INRIA]
- Aymen Salah Eddine Bouferroum [INRIA]
- Hazem Chaabi [INRIA]
- Selina Cheggour [UNIV LILLE]
- Lucien Dikla Ngueleo [INRIA, from Oct 2024]
- Emile Egreteau-Druet [INRIA, from Dec 2024]
- Tatiana El Jamous [SAFAR, from Sep 2024]
- Jana Koteich [INRIA, until Sep 2024]
- Marwa Slimene [INRIA]
- Jiali Xu [INRIA]
Technical Staff
- Khalil Ben Kalboussi [INRIA, Engineer, from Sep 2024]
- Etienne Profit [INRIA, Engineer]
- Alexandre Veremme [INRIA, Engineer, from Jun 2024]
Interns and Apprentices
- Amer Alzein [INRIA, Intern, from Sep 2024]
- Lucien Dikla Ngueleo [INRIA, Intern, from Apr 2024 until Sep 2024]
Administrative Assistants
- Lucille Colin [INRIA, Project manager]
- Solenne Fortun [INRIA, Project manager]
- Anne Rejl [INRIA]
2 Overall objectives
With the foreseen increase of communicating devices around the world, many challenges will arise. Among them, the most predominant ones are certainly the scarcity of the medium, the energy consumption, the lack of interoperability and the security of these devices and their data.
Our objectives are to address these different challenges for the self-organization of these Future Ubiquitous Networks. Our focus will be set on wireless heterogeneous communicating objets that feature different limitations and constraints such as hardware limitations (low computing and memory storage capacities), limited energy, potentially high mobility or hostile environment. By wireless, we mean any communication with no wire. Objects could thus communicate through traditional RF transmissions or any alternative way such as visible light communication (VLC) or molecular technologies. They can be heterogeneous in terms of hardware processing, mobility patterns (mobility can be undergone or controlled, unknown or predictable), communication technologies, etc. For all these families of devices, we will design holistic communication protocols to allow them to efficiently function and cooperate in a harmonious energy- and data-priority aware fashion. These protocols will focus on low communication layers (PHY, MAC and NET) and combine opportunistically heterogeneous device features to make a global efficient behavior emerge.
The goal of the FUN project team is to leverage the heterogeneity of the new communicating devices to override major rising issues. Heterogeneity and mobility will be seen as opportunities and strengths rather than flaws and exploited. Our protocols will foster the cooperation between devices in a secure, energy efficient and frugal way.
3 Research program
Objectives and methodology
To achieve our main objectives, we will mainly apply the methodology depicted in Figure 1 combining both theoretical analysis and experimental validation. Mathematical tools will allow us to properly dimension a problem, formally define its limitations and needs to provide suitable protocols in response. Then, they will allow us to qualify the outcome solutions before we validate and stress them in real scenarios with regards to applications requirements. For this, we will realize proofs-of-concept with real scenarios and real devices. Differences between results and expectations will be analyzed in return in order to well understand them and integrate them by design for a better protocol self-adaptation capability.
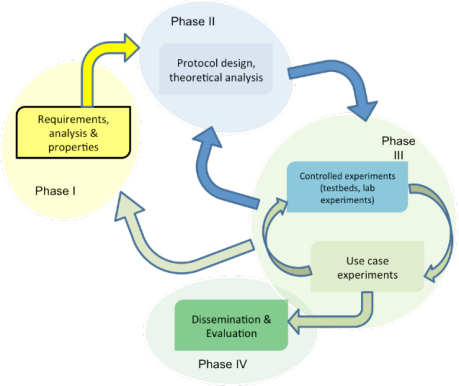
Methodology to be applied in FUN.
3.1 Research axes
To reach this overall objective, we will develop our research around the three following axes: i) Frugality and opportunism, ii) Security and iii) Interconnectivity. Note that these axes are not completely independent nor hermetic. A transversal axis will be the deployment and set up of experimental testbeds.
3.1.1 Frugality and opportunism
As the objects we consider are resource-limited and that they use a rare resource to communicate (wireless medium), all our solutions must be frugal and use as little resources as possible. A way to alleviate the energy consumption and the medium utilization is to reduce the data to send and/or to smartly decide when to send it, by what mean and to whom without jeopardizing the accuracy and completeness of the data. When to send a piece of data can indeed impact the resource utilization since in a dynamic environment, some interference could appear at different times; in a mobile environment, a piece of data could be carried rather than transmitted; in an energy-harvesting network, the amount of available energy could grow. We thus intend to closely analyse and understand interference impacts on different environments and contexts on one hand (as the research initiated in LumiCar, EthiCam, AgriNET projects) and to exploit them in the design of our protocols.
Deciding what data to send allows for a data reduction and resource savings. To do so, we will use machine learning techniques (e.g. Thompson sampling, Bayesian approaches, linear approaches, ARMA, Pearson sampling etc) that we will adapt to fit the specific context of the applications. The idea is to propose predictive algorithms to "guess" a data rather than transmitting it. This is among others what we are investigating in the AgriNET project.
In case of the availability of multiple communication technologies, the choice of this technology will impact the global system since all technologies do not provide the same QoS performances (delays, throughputs, etc) with different energy consumptions and do not face interferences the same way depending on the environment. We will thus analyse and understand all these specificities to combine them to get the best performances.
In all above mentioned cases, we will try to provide time and space depend protocols as frugal as possible but still meeting the application requirements and expectations. This will be done by opportunistically leveraging network particularities (multiple technologies, mobility, energy-harvesting, etc) based on experimental-driven behavioral analysis, as initiated with the collaboration with Sencrop.
3.1.2 Security
Security of wireless transmissions is a rising issue that gains importance with the increase of wireless devices. Our team has just started research work in security but we will pursue our efforts. Our goal will be to secure the wireless communications in different ways. Indeed, traditional security techniques (cryptography, firewalls, etc) cannot be applied in FUN because of their pervasive feature and limited resources. In terms of Security, we will focus on the lowest layers of the communication stack in order to first identify attacks that may appear at these levels and proposes i) recovering and healing solutions and ii) new solutions that are robust by design.
At the MAC layer, we will for instance investigate denial of sleep-like attacks that aim to make nodes deplete their energy quickly. At NET layer, we will investigate different routing protocols that are able to detect an abnormal behavior of a neighbor node to then exclude it from any network operation. This has obviously to be done locally and in a distributed way. In all cases, the same methodology will be applied: observe, understand and model, to then identify the threat or the malicious entity and finally heal. In some cases, we can leverage the characteristics of the communication technology to reinforce the security aspect, such as VLC that may allow Line-of-Sight (LOS) communications and for which certain types of attacks that can be effective for "traditional" wireless systems (i.e., jamming attacks) cannot be easily applied. The works initiated in the framework of the H2020 CyberSANE project, in the DGA grant and in DEPOSIA project, fall within this perspective.
3.1.3 Interconnectivity
Another challenge faced by FUN is their interconnectivity to traditional networks such as Internet and the data offloading. Because of their limited capacity, FUN devices may need to call for remote services. These latter are usually hosted in the cloud. But being served by the cloud implies sometimes long latency and uselessly congestion of the wired network. We will thus investigate how to get these services closer to the FUN devices to alleviate the energy consumption, reduce latency and network congestion. This will go from edge and mobile edge deployments to service distribution over more powerful heterogeneous devices. Our research will analyse devices needs and estimate in time and space the services to be deployed. When the service is expected to be temporary, mobile edge services could be deployed and so our investigations will include the self-deployment techniques. When some already deployed wireless devices feature more capacity, we can leverage this node heterogeneity to distribute the services over these nodes. The research conducted towards this third objective will call for adaptation of machine learning techniques to predict needs, to mobility modeling and cross-layer communication protocols. This has been initiated in the DRUID-NET project.
4 Application domains
The FUN research can be applied in various applications. We only cite here the ones on which we currently focus.
- Smart Agriculture: Wireless sensors are more and more deployed in remote fields and livestock for an accurate monitoring. This generates new challenges in terms of reliability, energy consumption and range as investigated in the D4SC and Agrinet projects.
- Vehicular networks: vehicles become smarter and smarter, providing new useful services. But communications between vehicles on the one hand and between vehicles and road infrastructures on the other hand raise a lot of challenges as investigated in the CORTESE project, by considering security aspects of the different communication technologies enabling the connected vehicles or with the :dot.dot company 5. Moreover, alternative technologies and interactions of traditional and unconventional communication technologies are considered in LumiCAR.
- Smart infrastructures: FUN research can also apply to different urban and civil infrastructure like road monitoring (as in the DEFI with CEREMA or SIRCAPASS project) or Smart Grids. In the project MLSysOps a full AI-based framework is implemented for autonomic end-to-end system management across the full cloud-edge continuum, that can be applied to different infrastructures.
- Logistic and traceability: RFID and IoT are the key technologies to enable large scale traceability. They are for instance investigated in the GoodFloow and AUtonomous Pack projects. Traceability is also investigated by the means of advanced technologies, that are the focus of ETHICAM project.
- Post disaster recovery: New services of different kinds (communications, processing, context analysis) need to be deployed quickly and efficiently after a disaster in order to support rescue operations. This requires adaptable and flexible resource deployment such as investigated in NEPHELE project.
5 Social and environmental responsibility
All protocols and algorithms designed and developed in the team are energy-efficient by design. Going further, especially in Research focus 1, we target applications that are environment-friendly and which aim to reduce a more global environmental footprint such as reducing the use of extra intrant in agriculture (such as water or fertiliser), enabling the reuse of packaging or less pollutant road and structures maintenance or with social concerns. This is reflected by the main topic of most of our collaborative projects and of the support from ADEME.
In the last few years, several solutions developed in the context of different projects in the team, are based on the integration of security aspects by design. In particular, the constrained and resource limitations of the IoT paradigm, that is at the core of the reasearch activities of the team, imposes a consideration of cyber-security solutions that explicitly account for these limitations. Advanced cyber-security approaches based on physical layer and cross-layer approaches have been recently developed in the context of European, National and Regional initiatives, accounting the social and environmental aspects by design.
6 Highlights of the year
6.1 Awards
- Valeria Loscri has been recognised as top 2% researcher for career in Networking, Artificial Intelligence, and Information and Communication in 2024.
- Valeria Loscri has been shortlisted by the CEFCYS - Cercle des Femmes de la CyberSécurité in the category 6 as Cyber Researcher in 2024.
- Prakriti Saxena has been awarded the i-PHD prize by the Government of France, through France2030 and Bpifrance for OptiWISE project in 2024.
6.2 Best paper awards
The FUN team received the best paper award in the DistInSys 2024 conference 12, and the best demo award in CIoT 2024 14.
7 New software, platforms, open data
7.1 New software
7.1.1 PILOT Dataset
-
Name:
Privacy-preserving data collectIon of wireLess cOmmunication Technologies.
-
Keywords:
Wireless network, Human mobility, Sensors
-
Scientific Description:
"PILOT dataset" is a privacy-preserving collection of wireless communication data from three technologies: WiFi, BLE (Bluetooth Low Energy), and LoRa (Long Range Radio), alongside sensor data (acceleration, roll, pitch). It is collected over 90 hours in various mobility scenarios, including static and mobile contexts, using Pycom FiPy devices. The dataset, which preserves privacy by masking sensitive information, is available on GitHub for use in human mobility studies and machine learning applications.
-
Functional Description:
PILOT dataset provides a new generation of collected data that would help in providing keys for studying human mobility or other applications. It is characterized by mainly two novel approaches for collecting data, at the level of Model type and Parameters recorded, as follows: 1) Collecting different types of data from sensors and wireless communication technologies at a time: WiFi probe-response, BLE beacons, LoRa packets, and from the sensors: Acceleration, Roll and Pitch information. 2) The data is collected in different mobility scenarios and mainly classified into two categories: Static vs Mobile. The overall collected data till now spans about 90 hours in total in different mobility scenarios collected using a Micropython enabled microcontroller called FiPy device. The dataset is released as a collection of text files and comma-separated values (CSV) files with mainly the timestamp, a unique identifier of the emitting device, RSSI (Received Signal Strength), and other information dedicated to each wireless technology. This dataset is privacy-preserving since it fully meets the GDPR specification, where the mac addresses and the device names are masked.
-
Contact:
Jana Koteich
7.1.2 my_ble
-
Name:
ESP-IDF my_ble component
-
Keyword:
Bluetooth
-
Functional Description:
This is a component campatible with ESP IDF V5.3.1 providing an API to use Apache MyNewt NimBLE host on ESP32 MCUs exposing simple to use predefined functions, yet giving full control over core functionalities like task handling, multiprocessing and semaphore enabled BLE scan checking.
-
Contact:
Khalil Ben Kalboussi
-
Participant:
Khalil Ben Kalboussi
7.1.3 LoRa WuR
-
Name:
librairie ESP-IDF pour module LoRa sx1261
-
Keywords:
Sx1261, LoRa, ESP32, ESP-IDF
-
Functional Description:
This is a library (in the form of a component) compatible with ESP-IDF V5.3.1 that enables the use of the SEMTECH SX1261 LoRa module with the ESP32(S3). The component is based on the low-level hardware driver provided by SEMTECH, which operates over the SPI bus, modified to include functions for sending, receiving, and packet detection in sleep mode (RxDutyCycle) in GFSK mode. The library provides functions for use in a normal mode, where it automatically handles tasks and SPI bus management internally, or in an advanced mode that offers full control over SPI bus management and process scheduling.
- URL:
-
Contact:
Khalil Ben Kalboussi
7.2 New platforms
SLICES
Participants: Nathalie Mitton, Lucille Colin, Solenne Fortun.
The FUN team is leading the deployment of the SLICES-FR research infrastructure, national node of the SLICES-RI ESFRI, also led by Inria and the FUN team.
7.3 Open data
We believe open software and open data collection or generation tools are mandatory in our research, to ensure reproducibility and repeatability. Therefore, we have built two main software tools. The first one relies on the SLICES/FIT IoT LAB open testbed and allows for the generation of network data. The second one allows for the collection of real communication traces. Both our tools are made available on open gitlab and the dataset either generated or collected are freely shared. A third dataset concerns the generation of data regarding hardware impairments in different reprogrammable devices, in order to develop RF fingerprinting on those devices and allowing the design of advanced authentication approaches. The software tools call to the enrichment of these datasets.
-
Sisyphe.
The Sisyphe tool 27 relies on the SLICES/FIT IoT-Lab large scale testbed and state-of-the-art software engineering techniques to produce, collect and share artefacts and datasets in an automated way. This makes easy to track the impact of software updates or changes in the radio environment both on a small scale, e.g. during a single day, and on a large scale, e.g. during several weeks. By providing both the source code for the trace generation as well as the resulting datasets, we hope to reduce the learning curve to develop such applications and encourage reusability as well as pave the way for the replication of our results. While we focus in this work on IoT networks, we believe such an approach could be used in many other networking domains. All generated datasets and open software are available here and in Zenodo. It has been then extended to include mobility in data generation. This extension is available here and exploited in different results such as in 3.
-
PILOT.
Pilot 17 dataset is a Privacy-preserving data collectIon tool of wireLess cOmmunication Technologies. The collected dataset is a collection of four jointly collected information in different mobility contexts. It includes three wireless communication technologies: WiFi probe-responses, BLE (Bluetooth Low Energy) beacons, and LoRa (Long Range Radio) packets, plus additional information: Acceleration, Roll, and Pitch, all collected at the same time. We provide the keys to reproduce such data collection and share the datasets already collected. The dataset is collected for approximately 90 hours, with a size of 200 MB using FiPy devices from Pycom and it is uploaded to GitHub. The dataset's utility is validated through the application of a classification machine learning model 4, 17 that determines the real-life situation of devices through the communication links monitored in different scenarios with an accuracy of 94%. Finally, we exploited this mobility status information to design an opportunistic routing protocol 19. Thus, we believe that such dataset is important for human mobility studies and applications of integrated sensing systems since it offers a new form of a classified collected data that does not exist in the already published datasets. All collected datasets and open software are available here.
-
PLA.
We implemented a full stack to perform device authentication, independently of the wireless communication technology used. In fact, the authentication approach is based on the hardware impairment of the devices and how these impairments impact the signal generated by wireless. In particular, we induced a combination of three impairments, Carrier Frequency Offset (CFO), Direct Current Offset (DCO), and Phase Offset (PO). For that, we considered reprogrammable devices, in order to design more critical scenarios, with close signatures for devices, namely very similar impairments on the same models of devices 1. The general code as well as the data have been submitted for artefact evaluation in the context of the ACSAC 2024 conference, and the contribution received three badges, code available, code reviewed, and code reproducible PLA-ACSAC.
8 New results
8.1 Attack detection and countermeasures
Participants: Valeria Loscri, Selma Yahia, Ildi Alda, Jiali Xu, Aya Moheddine, Aymen Bouferroum, Lucien Dikla Ngueleo.
In the context of the IoT paradigm, several new communication technologies are considered, that co-exist and may also interact. In this context, the security landscape is completely changing 25, by adding the vulnerability of each communcation technology and also by creating new ones. One key communication technology considered is based on optical signals and constitutes the basis of the optical wireless Communication (OWC) paradigm. In this context Visible Light Communication (VLC) is expected to enable a wide range of applications in the next generation wireless networks. These applications are recognized as sensitive and prone to dangerous threats. The specific characteristics of VLC systems make the traditional countermeasures adopted in radio-frequency-based systems not applicable, with a concrete need to conceive ad hoc solutions. Basing on these premises, in 7 we consider a physical layer perspective by analyzing the intrinsic properties of visible light signals so as to develop a secure by design VLC system to be used in downlink. In particular, we consider light bias application to the original signals, in order to improve the robustness of the wireless communication in respect of an external eavesdropper. This appraoch is developed by guaranteing the good level of illumination, in order to exploit the same infrastructure for illumination and communication.
A different approach to design a secure communication system is propsoed in 11, where the hardware impairments of devices are exploited to create unique signatures of emitting sources. a novel hybrid physical layer authentication (PLA) method designed to enhance security in multi-node networks by leveraging inherent hardware impairments. The approach specifically exploits carrier frequency offset (CFO), direct current offset (DCO), and phase offset (PO) as multi-attribute features, improving the verification process for authorized users and enhancing the detection of unauthorized devices. Machine learning (ML) models are developed to authenticate devices without prior knowledge of malicious characteristics, resulting in robust and reliable device authentication capabilities. Experimental evaluations conducted on a commercial software-defined radio (SDR) platform demonstrate the effectiveness of the proposed approach under varying signal-to-noise ratio (SNR) conditions. The hybrid PLA scheme integrates advanced feature extraction methods with finely-tuned ML models, optimized through controlled experiments to ensure high performance across diverse network conditions and attack scenarios.
Together with security approaches, an interesting subject to be investigated is trustworthiness, that we explicitly considered in a vehicular context in 10. Trustworthiness in wireless networks is an open challenge due to several features that should be taken into account. All the networking concepts should be updated accordingly, as well as physical layer features that influence the node transmission ability. Indeed, a trusted vehicle is expected to efficiently forward data packets, in order to reach the highest number of neighbors. At the same time, a trusted vehicle is expected to be well-recognized within the network, thanks to a high reputation degree. We consider the open challenge of trustworthiness node degree, based on both the reputation degree computed according to real-time interactions and past data, and on physical features of the wireless communication channel.
8.2 Visible Light Communication (VLC)
Participants: Valeria Loscri.
The lack of sufficient resources in the context of wireless communication systems led to the spectrum crunch phenomenon, pushing researchers to explore alternative technologies outside the RF band. Among many strategies that have been adopted to maximize the exploitation of these precious resources, Visible Light Communication (VLC) demonstrates a huge capacity to complement conventional RF technologies in plenty of applications. On the other hand, the arising of new communication technologies, cannot neglect the presence of already well-assessed communication paradigms. In 8, the co-existence of VLC and the long-term evolution (LTE) cellular network in a vehicular environment is explicitly investigated. The coordination of data transmission among different technologies is managed through a novel vertical handover mechanism, namely INVISIBLE2.0. This technique is triggered by the error probability to meet the 3GPP requirements on packet reception ratio while endorsing VLC as the preferred technology bearer. We demonstrate that INVISIBLE2.0 achieves a more stable latency, and energy efficiency based on a detailed power model represented here for VLC and LTE.
On the other hand, VLC and more in general Optical Wireless Communication (OWC) have been always regarded as technologies guaranteeng a strong immunity to Radio Frequency electromagnetic interference. However, as a matter of fact, no accurate studies have been realized in low cost practical implementations of this technology. For the establishment of the OWC in real scenarios it is paramount to have an electromagnetic characterization of the environment, considering the effects of Radio Frequency interference on system performance. A proper analysis of interference prevents Electromagnetic Compatibility issues between a Visible Light Communication system (VLC) and the other components of the architecture and, overall, underline critical frequencies that could be potentially exploited by electromagnetic attacks.
Based on these premises, we found paramount to realize an extended analysis of the effects caused by electromagnetic radiations on a typical VLC Tx-Rx pair has been realized 16. Two optical prototypes have been developed and tested in a controlled environment. Plane waves, generated at different power levels and in a wide frequency range, represent the intentional interference sources. The effects on data communication, considering Pulse Position Modulated (PPM) as useful optical signal, have been measured and shown. Effects on time domain and Bit Error Rate (BER) have been reported, demonstrating that this RF-immunity is not existing and showing the potential harmful effects of such a type of interference on an optical communication system.
8.3 Network observation and exploitation
Participants: Jana Koteich, Nathalie Mitton, Damien Wohwe Sambo.
Observing what the exchanges transitting on the wireless medium in terms of occupation, rate and durations is full of knowledge. We developed several tools to capture this medium business and characterise it. This allowed us to infer different features such as device mobility, QoS future requirements or network discovery.
8.3.1 Device mobility
The ubiquitous nature of mobile devices equipped with radio communication technologies made the collection of data a commonplace especially for studying human mobility. The collection of such datasets forms the intermediate results in many scientific research projects. Therefore, with the lack of datasets, collecting and publishing data should be seriously addressed since several scientific research is based on the gathering and analysis of measurement data. In 17, 18, we introduce the PILOT dataset, also referenced in 7.1.1, a Privacy-preserving data collectIon of wireLess cOmmunication Technologies.
The dataset is a collection of four jointly collected information in different mobility contexts. It includes three wireless communication technologies: WiFi probe- responses, BLE (Bluetooth Low Energy) beacons, and LoRa (Long Range Radio) packets, plus additional information: Acceleration, Roll, and Pitch, all collected at the same time. We provide the keys to reproduce such data collection and share the datasets already collected. The dataset is collected for approximately 90 hours, with a size of 200 MB using FiPy devices from Pycom and it is uploaded to GitHub. The dataset's utility is validated through the application of a classification machine learning model that determines the real-life situation of devices through the communication links monitored in different scenarios with an accuracy of 94%. Thus, we believe that such dataset is important for human mobility studies and applications of integrated sensing systems since it offers a new form of a classified collected data that does not exist in the already published datasets. This knowledge is latter exploited to ehance routing protocols as explained in Section 8.6.
8.3.2 Network servicing
Internet of Things (IoT) applications generate tremendous amounts of data streams which are characterized by varying Quality of Service (QoS) indicators. These indicators need to be accurately estimated in order to appropriately schedule the computational and communication resources of the access and Edge networks. Nonetheless, such types of IoT data may be produced at irregular time instances, while suffering from varying network conditions and from the mobility patterns of the edge devices. At the same time, the multipurpose nature of IoT networks may facilitate the co-existence of diverse applications, which however may need to be analyzed separately for confi- dentiality reasons.
Hence, in 6, we aim to forecast time series data of key QoS metrics, such as throughput, delay, packet delivery and loss ratio, under different network configuration settings. Additionally, to secure data ownership while performing the QoS forecasting, we propose the FeDerated Temporal Sparse Transformer (FeD-TST) framework, which allows local clients to train their local models with their own QoS dataset for each network configuration; subsequently, an associated global model can be updated through the aggregation of the local models. In particular, three IoT applications are deployed in a real testbed under eight different network configurations with varying parameters including the mobility of the gateways, the transmission power and the channel frequency. The results obtained indicate that our proposed approach is more accurate than the identified state-of-the-art solutions. This result relies on the sisyphe tool described in Section Software and 7.3.
8.3.3 Network discovery
Due to their limited resources, IoT devices are constantly striving to find a balance between energy consumption and performance. In this ongoing endeavor, the communication module frequently emerges as the foremost contributor to energy consumption. Among various communication technologies, Bluetooth Low Energy (BLE) stands out as a promising candidate due to its lightweight architecture and excellent performance. Despite recent advances in BLE optimization, the Neighbor Discovery Process (NDP) remains a highly energy-cost task. To enhance energy efficiency during this operation, we propose in 23 a new approach for the NDP that leverages the multicore architecture of a recent microcontroller to dynamically adjust the scanning duration based on the number of devices to discover. Intensive simulations have shown that a fixed scanning duration can be avoided by ending the NDP after discovering the required number of devices. Our proposal demonstrates a reduction in energy consumption through intensive simulations and a robust validation methodology. Furthermore, real-world experiments indicate that our approach can achieve up to 50% energy savings compared to a 1-second scan when only one core is used during the NDP.
8.4 Wireless network analysis for vehicular networks
Participants: Nathalie Mitton, Valeria Loscri.
The protocols for vehicular networks are mostly developed, tested and evaluated through simulations in network simulators first before implementing and experimenting them in the real-world. For simulating vehicular networks, various mobility datasets are made publicly available by SUMO that can be imported into network simulators (e.g., OMNeT++, NS-3). The development of protocols for vehicular networks requires analyzing some common metrics (such as distribution of vehicles, contact duration between vehicles and time to meet new neighbors). Therefore, researchers are high likely to implement and analyse these metrics as a first step. In 22, we analyse the common required metrics for vehicular networks using OMNeT++ and Veins by using SUMO vehicular mobility datasets of Ireland urban and highway scenarios for rush and non-rush hours. We have provided our code publicly available as open-source that will be time-saving for researchers who start developing protocols for vehicular networks. We believe such analysis results can help in designing communication or dissemination protocols in vehicular networks and understanding vehicular traffic for further applications.
In 9, we first leverage all the knowledge achieved in this first study to draw the specific features of a vehicular network at different times and spaces. This study then allows us to adapt a dynamic neighbour discovery protocol to the specific case of vehicular-to-vehicular communications to propose VANP (Vehicular Adaptive Neighbour Discovery Protocol). VANP is a fully distributed and software-based solution that sends beacons at an optimal frequency without knowing it a priori. The objective is to reduce the frequency at which HELLO messages are sent to save bandwidth and energy while still preserving the quality of the neighbour discovery. Through extensive simulations run on real datasets, we show that the optimal HELLO frequency can be reached by maintaining a constant optimal turnover, independent from the speed of the nodes and by aiming at this turnover, nodes automatically use the optimal HELLO frequency. Results show that VANP allows the discovery of relevant neighbours by missing at most two neighbours over all scenarios and reducing the number of HELLO messages up to twice, hence saving bandwidth and energy.
8.5 UAV detection and placement
Participants: Ildi Alla, Valeria Loscri, Selma Yahia.
Advances in Unmanned Aerial Vehicles (UAVs) empower a plethora of applications but also raise significant security and privacy challenges. Effective UAVs detection systems are crucial for mitigating these risks. In 21 we considered the challenges associated with real-world testing and the limitations of existing simulation methodologies for validating and evaluating UAVs detection protocols. A novel, realistic, and extensible framework is introduced, which includes a MATLAB-based surveillance system, a Python-based detection module utilizing Stacked Denoising Autoencoder (SDAE) and Local Outlier Factor (LOF) algorithms, and a hybrid database of both real and synthetic wireless RF signals. The synthetic wireless dataset is generated by the proposed surveillance system module. The alignment between the synthetic and real data is validated with an average Mean Squared Error (MSE) of less than 0.25. The detection module proves highly effective, achieving 96%
accuracy in correctly classifying Wi-Fi signals and 88%
accuracy in identifying UAV signals as anomalies (outliers). This innovative approach facilitates ongoing research and development in UAV detection, with the extensibility to incorporate new RF signal types and UAV models.
Another important point related to UAVs/Drones is their geo-localization. Computing an accurate and precise geolocation of these drones, especially in outdoor environments, remains challenging. In 15 we consider outdoor 3-dimensional (3D) drone geolocation techniques based on Radio Frequency (RF) signals. In particualr, we consider a RF-based 3D drone geolocation dataset, and then apply and compare various geolocation techniques, ranging from geometrical-based to machine learning-based methods. We further propose a new hybrid method blending the two above categories of geolocation techniques, that achieves an average 3D error of the order of 11.7 meters within a search volume of about 520×560×115m3, significantly below the one achieved with geometrical-based tech- niques, and with a reduced computational complexity compared to the regular machine-learning based techniques.
Another important aspect related to drones is their deployment. Deploying UAVs as aerial base stations requires careful consideration of crucial design factors, including three-dimensional (3D) placement and performance optimization tailored to specific applications. In 24, the 3D placement of multiple UAVs, acting as aerial base stations, is investigated in a dynamic user scenario. First, a closed-form expression for the coverage probability is derived. Then, to maximize the network coverage and sum rate while ensuring reliable and energy efficient system, a joint multiobjective optimization problem is formulated considering the real-time user movements. To solve the problem, an improved Chaos-based Bonobo Optimizer (CBO) scheme is proposed which combines chaotic maps with the Bonobo Optimizer (BO) algorithm. The obtained results demonstrate the superior performance of the proposed approach compared with different benchmark algorithms.
8.6 Routing in wireless networks
Participants: Nathalie Mitton, Jana Koteich, Adriana Arteaga Arce.
The development of delay tolerant networks (DTNs) has been driven by the need to overcome communication barriers in situations where traditional network assumptions do not apply. DTNs are designed to function effectively in situations where traditional networks fail due to limited connectivity, extended delays, and recurrent disruptions. They are characterised by their ability to store and forward data, adapt to changing network conditions, and maintain communication even in the face of disruptions. They are typically decentralized, self-organizing and fault tolerant.
Inspired by the PRoPHET protocol, in 13 we present the R-PRoPHET protocol to provide an intermittently connected network in a rural context, where the variable mobility of vehicles requires flexibility to model the encounters between nodes. Our protocol incorporates information about the time between encounters in the past to make smooth adjustments in parameters that impact the decision to relay messages. The R-PRoPHET protocol implements two forwarding strategies to manage the trade-off between the delivery ratio and the number of messages relayed along the network. Results showed that R- PRoPHET increases the delivery ratio by up to 20% and reduces the average latency by up to 16% compared to PRoPHET. The overhead produced by R-PRoPHET is around two times more than PRoPHET, which is part of the trade-off of increasing the average delivery ratio and reducing the average latency.
In 19, we propose 'Baton-relay', a mobility context-aware routing protocol in DTN. This protocol relies on low-cost communication and storage devices that can embed different communication technologies, resulting in a global privacy-preserving data-sharing system based on natural crowd mobility. It relies on the exploitation of the PILOT DATASET described in Section 7.3 and on the mobility inference achieved in 26 as detailed in Section 8.3.
First, we analyse crowd mobility patterns to assign a delivery probability for a message based on its mobility pattern. The device will estimate its real-life situation, then exploits this information to take a forwarding decision. We tested and validated the approach using the ONE simulator, which is designed for an opportunistic network environment. The idea of Baton-relay is simple, not based on extensive mathematical calculations, does not require a huge memory or buffer, yet is robust, guaranteeing a reasonable probability of delivery and it preserves privacy. Results show that Baton-relay achieves a significant improvement for the buffer time average, number of hops and copies overhead compared to other routing protocols.
Networks with large amounts of transmissions often involve redundancies in the transmitted data, which results in high energy consumption for low utility. For example, the measurement of temperature at a point A and another measurement of temperature at a second point close to A. Using a well-chosen prediction algorithm, estimations of a node's measurements could be an acceptable alternative to transmitting the real values. In 20, we extend our previous work designed for leveraging correlation between two nodes to explore this correlation between multiple nodes over a multi-hop network. Results show that we can reach up to 250 times less data while not losing the information which validates our approach as we can see in the evaluation section.
8.7 Continuum IoT/edge/Cloud
Participants: Nathalie Mitton, Carol Habib, Alexandre Veremme, Adriana Arteaga Arce.
The cloud-to-edge-to-IoT continuum represents a seamless flow of data processing and management, spanning from centralized cloud services to distributed edge computing and interconnected IoT devices. This paradigm can become very challenging in real implementations, especially in the presence of multiple stakeholders using proprietary and heterogeneous software and hardware. The Horizon Europe NEPHELE project proposes the virtualization of IoT devices through a specific software stack called Virtual Object Stack (VOStack) that pro- motes openness and interoperability.
In 12, we present an implementation of VOStack using W3C Web of Things (WoT) standard in a post-disaster domain for two different types of IoT devices: a ground robot (Turtlebot2) for navigation and mapping in an unknown environment, and a Raspberry Pi 3 acting as a wireless sensor network gateway. This stack, proposed by the European Horizon NEPHELE programme, promotes openness and interoperability in the cloud-to-edge-to-IoT continuum. We propose an application graph for the resulting hyper-distributed application (HDA) and present our first implementation to validate the proposed solution. In the demo presented in 14, we present the implementation of a virtualized Wireless Sensor Network following a specific software stack called Virtual Object Stack (VOStack). The demonstration shows a wireless sensor monitoring application distributed along the continuum, validating the endto-end communication among FiPy-based sensor nodes and a web application through the virtual object of a Wireless Sensor Network Gateway.
9 Bilateral contracts and grants with industry
9.1 Bilateral Grants with Industry
Participants: Valeria Loscri.
- NavalGroup (2024): This collaboration aimed to develop a full end-to-end OWC system between a ship and a receiver at the ground. It has been established in the context of OptiWISE framework.
9.2 Start-up
Participants: Valeria Loscri.
Valeria Loscri initiated a project to establish a secure Optical Wireless Communication (OWC) between nodes at a distance of around 1 to 2 km based on her past expertise on OWC and VLC wireless communication systems on which she also patented the idea1. Prakriti Saxena, an engineer supervised by Valeria, led the project in the ISS programme in September 2023.
1) OPTIWise represents one key activity in terms of security communication technologies and the main aim is to develop a final commercial prototype. The different advancements realised in about more than one year, permitted to understand the main limitation of in-lab experiments and to acquire a better background of the technology. 2) The action was supported by Inria under the framework of ISS (Inria Startup Studio). In this context, Prakriti Saxena developed a very large networking of potential stakeholders, both in military domain and for civil application. In particular, a sub-contract with NAVAL Group has been established in the military context, for which the main aim is to develop an end-to-end reliable and secure communication between a ship and the ground. It is not possible to further develop the content of the contract because of an NDA contract that has been signed. On civil part, several telecom and other companies, as Accelleran NV, Signify, CAPGEMINI, have expressed their interest in the technology. A prematuration project, FRAME xG has been submitted to support the further prototype development. 3) Targeted end-users are in the military domain and for civil applications. Just as en example, based on different discussions had with different companies, it has been clear that wired fibre based communication cannot meet all the user requirements, above all when these requirements are dynamic, as in the case of high arise of the demand related for example to specific events as Olympic Games. In this context, the proposed solution can meet these dynamic needs, with similar performance of the wired version and reduced costs in respect of other potential concurrent solutions. 4) The major steps were related to the passage from the in-lab to the prototype solution. Valeria Loscri followed and is following the different technical evolutions and is playing the role of technical expert. 5) The solutions have been also validated in the PhLAM Lab at University of Lille and there are still some missing steps to make it a complete prototype. The realisation of this prototype will permit the creation of the start-up.
10 Partnerships and cooperations
10.1 International initiatives
10.1.1 Associate Teams in the framework of an Inria International Lab or in the framework of an Inria International Program
AGRINET
-
Title:
Wireless accurate monitoring for a smarter agriculture
-
Duration:
2020 -> 2024
-
Coordinator:
Riaan Wolhuter (wolhuter@sun.ac.za)
-
Partners:
- Stellenbosch University Matieland (Afrique du Sud)
-
Inria contact:
Nathalie Mitton
-
Summary:
Sustainable food security depends on proper plant and crop management respectful of soils and natural re- sources, such as water. To address these constraints, AGRINET developed a flexible, rapidly deployable, biological/agricultural data acquisition platform and associated machine learning algorithms to create advanced agricultural monitoring and management techniques, to improve crop management and use of natural resources.
10.2 International research visitors
10.2.1 Visits of international scientists
Other international visits to the team
- Emi Dreckmeyr spent one month at Inria from Stellenbosch University in May 2024.
- Nikola Schuster spent one month at Inria from Stellenbosch University in September 2024.
10.2.2 Visits to international teams
Research stays abroad
Participants: Ildi Alla.
-
Visited institution:
North Eastern University, Boston
-
Country:
USA
-
Dates:
June - August 2024
Participants: Jiali Xu.
-
Visited institution:
Padova University
-
Country:
Italy
-
Dates:
Oct. - Jan. 2025
10.3 European initiatives
10.3.1 Horizon Europe
NEPHELE
Participants: Amer Alzein, Adriana Arteaga Arce, Hazem Chaabi, Carol Habib, Nathalie Mitton, Alexandre Veremme.
NEPHELE project on cordis.europa.eu
-
Title:
A LIGHTWEIGHT SOFTWARE STACK AND SYNERGETIC META-ORCHESTRATION FRAMEWORK FOR THE NEXT GENERATION COMPUTE CONTINUUM
-
Duration:
From September 1, 2022 to August 31, 2025
-
Inria contact:
Nathalie Mitton
-
Summary:
The vision of NEPHELE is to enable the efficient, reliable and secure end-to-end orchestration of hyper-distributed applications over programmable infrastructure that is spanning across the compute continuum from Cloud-to-Edge-to-IoT, removing existing openness and interoperability barriers in the convergence of IoT technologies against cloud and edge computing orchestration platforms, and introducing automation and decentralised intelligence mechanisms powered by 5G and distributed AI technologies.
SLICES-PP
Participants: Lucille Colin, Solenne Fortun, Nathalie Mitton, Alexandre Veremme.
SLICES-PP project on cordis.europa.eu
-
Title:
Scientific Large-scale Infrastructure for Computing/Communication Experimental Studies - Preparatory Phase
-
Duration:
From September 1, 2022 to December 31, 2025
-
Inria contact:
Nathalie Mitton
-
Coordinator:
Nathalie Mitton
-
Summary:
SLICES-RI (Research Infrastructure), included in the 2021 ESFRI roadmap, aims to build a large infrastructure needed for the experimental research on various aspects of distributed computing, networking, IoT and 5/6G networks. It will provide the resources needed to continuously design, experiment, operate and automate the full lifecycle management of digital infrastructures, data, applications, and services. The SLICES-PP (Preparatory Phase) project aims to validate the requirements to engage into the implementation phase of the RI lifecycle (by setting the policies and decision processes for the governance of SLICES-RI, settling the final technical architecture design, engaging member states and stakeholders).
MLSysOps
Participants: Valeria Loscri, Jiali Xu.
MLSysOps project on cordis.europa.eu
-
Title:
Machine Learning for Autonomic System Operation in the Heterogeneous Edge-Cloud Continuum
-
Duration:
From January 1, 2023 to December 31, 2025
-
Inria contact:
Valeria Loscri
-
Summary:
The MLSysOps project addresses challenges of scalability, heterogeneity, security, dynamics and transparency to enable autonomic, efficient and adaptive end-to-end system management on the heterogeneous and dynamic edge-cloud continuum. To this end, MLSysOps (i) disassociates the management from the control of continuum resources, (ii) introduces an AI-driven control and management framework which interfaces with off-the-shelf management mechanisms, and (iii) employs a hierarchical, distributed, explainable and evolving AI architecture for autonomic system operation.
10.3.2 Other european programs/initiatives
NEWFOCUS
Participants: Valeria Loscri.
-
Title:
European network on future generation optical wireless communication technologies
-
Duration:
September 2020 - September 2024
-
Inria contact:
Valeria Loscri
-
Summary:
The COST Action NEWFOCUS will propose truly radical solutions with the potential to impact the design of future wireless networks. Particularly, NEWFOCUS aims to establish optical wireless communications (OWC) as an efficient technology that can satisfy the demanding requirements of backhaul and access network levels in beyond 5G networks. This also includes the use of hybrid links that associate OWC with radiofrequency or wired/fiber-based technologies. Towards this vision, NEWFOCUS will carry out a comprehensive research programme under two major pillars. The first pillar is on the development of OWC-based solutions capable of delivering ubiquitous, ultra-high-speed, low-power consumption, highly secure, and low-cost wireless access in diverse application scenarios. The developed solutions will in particular support Internet-of-Things (IoT) for smart environments with applications in vertical sectors. The second pillar concerns the development of flexible and efficient backhaul/fronthaul OWC links with low latency and compatible with access traffic growth.
BeingWise
Participants: Valeria Loscri, Ildi Alla.
-
Title:
Being Wise COST ACTION
-
Duration:
2023-2027
-
Action Chair and Scientific Holder:
Valeria Loscri
-
Summary:
The always-connected world we are living in, gives us an unprecedented plethora of new advanced services and automated applications requiring, more and more, less human intervention due to the increased integration of Machine Learning (ML), Artificial Intelligence (AI) approaches and sophisticated emerging wireless technologies.
On the other side, this connected world opens new breaches and creates new potential vulnerabilities for smart advanced cyber-attacks, namely attacks and offender relying on ML/AI and advanced wireless technology integration, to make their attack more effective and less detectable. If an increasing awareness by the users could help to contrast the security issues, it is not sufficient against the new generation of cyber-attacks. In this context, a drastic paradigm shift, putting human-being in the loop for the conception of novel and more effective cyber-security solutions, must be considered.
Human-beings have a double role in the cyber-connected world: as potential offender and potential victim. The focus of BEiNG-WISE will be on how these different human-being features can be combined with the advanced technological characteristics, in order to conceive non-conventional, responsible by design, cyber-security solutions accounting for both these factors. In this complex connected system, another fundamental aspect that needs to be accounted to, is the legal one, related to the conception of solutions that can be effectively employed in the real world. Also, legal aspects should be considered at the design stage. The Action relies on cross-domains expertise, ranging from cybersecurity, wireless communication technology, data science, sociology, psychology and law.
10.4 National initiatives
GoodFloow
Participants: Damien Wohwe Sambo, Nathalie Mitton.
-
Title:
ADEME GoodFloow Project
-
Duration:
October 2021 - June 2024
-
Coordinator:
GoodFloow
-
Inria contact:
Nathalie Mitton
-
Summary:
The goal of this project, funded by ADEME, is to design a very energy efficient node to manage reusable packaging in a more sustainable way by combining enhanced IA techniques, wake up radio and multi MAC layers.
AutonomousPack
Participants: Khalil Ben Kalboussi, Carol Habib, Nathalie Mitton.
-
Title:
ADEME AutonomousPack Project
-
Duration:
September 2023 - August 2026
-
Coordinator:
GoodFloow
-
Inria contact:
Nathalie Mitton
-
Inria participants:
Carol Habib , Nathalie Mitton
-
Summary:
The goal of the AUTONOMOUS PACK project is to push forward the achievements of the GoodFloow project by design a very energy efficient node to manage reusable packaging in a more sustainable way by combining enhanced IA techniques, wake up radio and multi MAC layers.
ANR NeMIoT
Participants: Valeria Loscri, Lucien Dikla Ngueleo.
-
Title:
Detection and geolocation of an illegitimate electromagnetic source with AI
-
Duration:
Jan. 2024 - Dec. 2026
-
Coordinator:
Univ. Lyon 1
-
Inria contact:
Valeria Loscri
-
Summary:
NEMIoT aims at (i) designing a solid framework to model, analyse and forecast the actual behaviour of IoT devices when placed in an actual IP network infrastructure as well as their impact on the hosting network infrastructure itself and (ii) developing original cross-layer solutions to finely and quickly detect and/or mitigate potential anomalies resulting from the introduction of IoT devices. To do that, NEMIoT will provide the necessary analytical methods and tools, establish a step-by-step methodology thought to be automated, and demonstrate their efficiency on testbeds with real-life IoT devices.
ANR DEPOSIA
Participants: Valeria Loscri.
-
Title:
Detection and geolocation of an illegitimate electromagnetic source with AI
-
Duration:
October 2021 - September 2024
-
Coordinator:
Virginie Deniau
-
Inria contact:
Valeria Loscri
-
Summary:
DEPOSIA focuses on the detection and geolocation of various radio frequency signal sources in order to thwart attacks on connected systems and infrastructures. The sources considered are elements which by their characteristics or their position, present an illicit character and which threaten the people security or the infrastructures. For outdoor cases, we consider drones flying over forbidden areas, telecommunication jammers, spoofing signal transmitters or wireless connected sensors used to introduce false data in monitoring platforms. For indoor cases, we also consider jamming or spoofing sources that can cause denial of service within networks or infrastructures, or fake access points that aim to carry out man-in-the-middle attacks to intercept information.
SIRCAPASS, BPI
Participants: Nathalie Mitton.
-
Title:
Monitoring road infrastructure using passive sensors
-
Duration:
June 2024 - June 2028
-
Coordinator:
SilMach
-
Summary:
This project aims to provide an operational response to the challenges associated with the preventive monitoring of bridges and the planning of their maintenance. SIRCAPASS will propose an innovation that breaks with current practices and concepts, based on the use of energy-free sensors. This project contributes to the first research focus.
ROAD-AI, common DEFI Inria and Cerema
Participants: Nathalie Mitton.
-
Title:
Routes et ouvrages d'art Diversiformes, Augmentés et intégrés
-
Duration:
July 2021 - June 2025
-
Coordinator:
Nathalie Mitton
-
Summary:
Integrated management of infrastructure assets is an approach which aims at reconciling long-term issues with short-term constraints and operational logic. The main objective is to enjoy more sustainable, safer and more resilient transport infrastructure through effective, efficient and responsible management. To achieve this, CEREMA and Inria are joining forces in this Inria Challenge (DEFI) which main goals are to overcome scientific and technical barriers that lead to the asset management of tomorrow for the benefit of road operators: (i) build a “digital twin” of the road and its environment at the scale of a complete network; (ii) define “laws” of pavement behavior; (iii) instrument system-wide bridges and tunnels and use the data in real time; (iv) define methods for strategic planning of investments and maintenance.
10.5 PEPR
The FUN team is involved in PEPR Networks of the future (PC6 and PC7), PEPR Cloud (PC8) and PEPR MobiDec (PC 3).
PEPR Network of the Future - Just Enough Network
Participants: Nathalie Mitton, Emile Egreteau-Druet.
-
Title:
PEPR NoF JEN
-
Duration:
2023 - 2028
-
Inria contact:
Nathalie Mitton
-
Summary:
Jointly with the Inria AVALON team and the AIVANCITY school, Inria FUN investigates the full life cycle of IoT-based 5G Solutions for Smart Agriculture in order to design holistic system for data collection in agriculture that take account of the full environmental footprint.
PEPR Network of the Future - FITNESS
Participants: Nathalie Mitton, Valeria Loscri, Aymen Salah Eddine Bouferroum, Marwa Slimene, Amira Mourad.
-
Title:
PEPR NoF FITNESS
-
Duration:
2023 - 2028
-
Inria contact:
Nathalie Mitton and Valeria Loscri
-
Summary:
FUN collaborates in WP2 and WP8 of this project. In WP2, Industry 4.0, we consider Industrial internet of Things (IIoT) and invetigate the security aspects related to the co-existence and interaction of different wireless communication technologies. In WP2, we investigate a whole hierarchical architecture, managing in an effective, energy-ware way trust model between resource-constrained and heterogeneous nodes. In WP3, we design a Collaborative Security and Remote Audit of V2X Communications, namely SCAR2X, aiming at a global security solution.
PEPR MobiDec
Participants: Nathalie Mitton.
-
Title:
PEPR Mobidec DataFactory
-
Duration:
2023 - 2026
-
Inria contact:
Nathalie Mitton
-
Summary:
In collaboration with Inria TRIBE and COATI teams, we build an open source easy-to-use software tool able to collect and generate data traffic over different wireless network technologies and to infer some mobility characteristics from it.
PEPR Cloud
Participants: Nathalie Mitton.
-
Title:
PEPR Cloud PC SILECS
-
Duration:
2024 - 2031
-
Inria contact:
Nathalie Mitton
-
Summary:
This project aims to build the research infrastructure to allow reproducible research in the full cIoT/edge/cloud continuum and contributes to the set up and deployment of SLICES-RI.
10.6 Regional initiatives
STIMULE CORTESE
Participants: Valeria Loscri, Selma Yahia.
-
Title:
CORTESE: Intelligent CO-existence of Communication Wireless Technologies for Secure and Intelligent applications
-
Duration:
Jan. 20233 - Dec. 2025
-
Inria contact:
Valeria Loscri
-
Summary:
This project aims at the coexistence of different technologies of wireless communication, in the vehicular context by investigating methods based on a sustainable Artificial Intelligence to select the most relevant technology to improve performance, reliability to guarantee increased robustness against cyber attacks. Given the high dynamics of the environment, learning approaches developed must be able to respond in real time with a particular focus on durability and security of wireless networks.
11 Dissemination
Participants: Valeria Loscri, Nathalie Mitton, Carol Habib.
11.1 Promoting scientific activities
11.1.1 Scientific events: organisation
Chair of conference program committees
- Valeria Loscri is/was Privacy and Security track chair at WF-IoT 2024, Symposium Chair of Wireless Communications Symposium, Medium access control and Networking Track chair at WCNC 2024 and Short Papers and Demo Session chair of WiMob 2024.
- Nathalie Mitton is/was co-TPC chair of DCOSS 2024, WiMob 2024, FCN 2024 and ICIN 2025. She was Tuto and workshop co-chair of EWSN 2024.
- Adriana Arteaga Arce, Aya Moheddine, Selma Yahia, Jana Koteich and Damien Wohwe Sambo were TPC co-chairs of UN3E 2024.
- Jana Koteich and Damien Wohwe Sambo were TPC co-chairs of LS-NOT 2024.
Member of the conference program committees
- Valeria Loscri has been a TPC member of ESORICS 2024, IEEE CSN 2024, PerCom 2024, Infocom 2024.
- Nathalie Mitton has been a TPC member of Infocom 2024, DCOSS 2024, Percom 2024.
- Carol Habib has been a TPC member of ICIN 2025, MenaComm 2025, WiMob 2024.
11.1.2 Journal
Member of the editorial boards
- Valeria Loscri is Associate Editor of IEEE Transactions on Information Forensics and Security (since 2022), IEEE Communications Survey and Tutorials (COMST, since 2020), Elsevier ComCom (since 2021), Frontiers in Communications and Networks, ITU-FET Journal, IEEE Transactions on Nanobioscience journal since 2017, of Elsevier Computer Networks journal since 2016, of Robotics Software Design and Engineering, of the International Journal of Advanced Robotic Systems since 2016, of Elsevier Journal of Networks and Computer Applications (JNCA) journal since 2016, of Wiley Transactions Emerging Telecommunications Technologies since 2019.
- Nathalie Mitton is an editorial board member of Adhoc Networks since 2012, of IET-WSS since 2013, of Wireless Communications and Mobile Computing since 2016, of Journal of Interconnection Networks since 2021.
11.1.3 Invited talks
- Valeria Loscri was invited speaker for the CTO Award Ceremony organised by CRIP in November 2024.
- Valeria Loscri was invited speaker at the 5G/6G Industrial Day in Stockholm organised by RISE in October 2024.
- Valeria Loscri was invited speaker at the Joint 6G-PHYSEC & INTERACT Workshop on 6G Technologies and PHY Layer Security.
- Valeria Loscri was invited at the RoundTable of Informatic Security and Social and Human Science organized by the GDR Sécurité Informatique and GDR Internet, IA et Societé.
11.1.4 Scientific expertise
- Valeria Loscri has been appointed as FWO chair for Fundamental Research Panel (2024). Valeria Loscri was FWO expert panel member for the PhD fellowship-Fundamental Research and for the Postdoc fellowship-Fundamental Research.
- Valeria Loscri has been appointed as evaluator expert of European Union COST Action.
- Nathalie Mitton has been appointed as scientific expert to evaluate projects submitted to ANR, South Africa's National Research Foundation (NRF), NSERC (Canada) and NSC (Poland), Bourses L'Oréal FRANCE, Polish National Science Centre and BPI.
- Nathalie Mitton is an external expert of scientific board for INRAE, IRIT lab and ESISAR.
11.2 Teaching - Supervision - Juries
11.2.1 Teaching
- Master: Valeria Loscri, Objets Communicants, 24h (Mineure Habitat Intelligent), Ecole des Mines de Douai, France
- Master: Nathalie Mitton, Wireless networks, 16h eqTD (Master TC), Université de Lille, France
- Master: Carol Habib, Wireless sensor networks, 16h eqTD (Master IdO), Université de Lille, France
- Master: Carol Habib, Smart objects, 10h CM + 12h TP, Ecole Centrale de Lille, France
- Master: Carol Habib, Industrial Internet of Things, 10h CM, Ecole Centrale de Lille, France
11.2.2 Supervision
- PhD defended:
- Jana Koteich, Context aware opportunistic forwarding strategy, Université de Lille, 2021-2024, Nathalie Mitton 26
- PhD in progress:
- Aymen Bouferroum, Vulnerability detection, trust and authentication methods applied to multi-technology communication in Industrial IoT (IIoT), Université de Lille, 2023-2026, Valeria Loscri
- Selina Cheggour, Cell-free approaches in wireless networks, Université de Lille, 2023-2026, Valeria Loscri
- Marwa Slimene, Blockchain-based security and audit for IoT and V2X communications, Université de Lille, 2023-2026, Nathalie Mitton
- Jiali Xu, Anomaly and attack detection in intelligent, deep systems with heterogeneous, reprogrammable nodes, Université de Lille, 2023-2026, Valeria Loscri
- Hazem Chaabi, Adaptive deployment of a distributed wireless monitoring network and edge services using a fleet of wireless robots, Université de Lille, 2022-2025, Nathalie Mitton
- Ildi Alla, Monitoring for detection and localisation of cyber attacks in wireless networks, Université de Lille, 2022-2025, Valeria Loscri
- Lucien Dikla Ngueleo, Attack and anomaly detection in IoT, Université de Lille, 2024-2027, Valeria Loscri and Kevin Jiokleng
- Emile Egreteau-Druet, Analyzing full life cycle of IoT based 5G solutions for smart agriculture, ENS Lyon, 2024-2027, Nathalie Mitton and Laurent Lefevre, Inria AVALON
- Tatiana Al Jamous, Smart Grid management for university campus, Université de Lille, 2024-2027, Nathalie Mitton, Carol Habib and Jad Nassar (Antonine Univ., Lebanon)
11.2.3 Juries
- PhD committees:
- Valeria Loscri is/was member of the following PhD thesis committees:
- Maugan de Murcia, University of Poitiers, chair
- De Biasio Alvise, University of Padua
- Montagna Andrea, University of Padua
- Pardini Susanna, University of Padua
- Tricomi Pierpaolo, University of Padua
- Visintin Alessandro, University of Padua, reviewer
- Yuan Ying, University of Padua
- Waleed Bin Qaim, Tampere University, opponent
- Eros Innocenti, Guglielmo Marconi University, reviewer
- Runbo Su, University of Lorraine, reviewer
- Alix Jeanerot, University of Lyon, INSA, reviewer
- Aurélien Chambon, University Gustave Eiffel, reviewer
- Francesco Paolo Saccomanno, University of Calabria, reviewer
- Amani Aou Rida, University of Strasbourg
- Nathalie Mitton is/was member of the following PhD thesis committees:
- Pierre Laclau, UTC, reviewer
- Evelyne Akopyan, ENSEEITH, reviewer
- Samuel Pelissier, INSA Lyon, reviewer
- Fadhila Tlili, UTT
- Aimé Cédric MUHOZA, Université Clermont Auvergne
- Alamy Toure, UPHF, chair
- Lucas Magnana, INSA Lyon, reviewer
- Ayush Sinha, IIIT Allahabad, India, reviewer
- Valeria Loscri is/was member of the following PhD thesis committees:
- HDR committees:
- Valeria Loscri was a member of the following HDR committe:
- Stéphanie Sahuguede, University of Limoges, reviewer
- Nathalie Mitton was a member of the following HDR committees:
- Rahim Kacimi, Univ. Toulouse
- Walid Bechkit, INSA Lyon, reviewer
- Valeria Loscri was a member of the following HDR committe:
- Research selection committees:
- Valeria Loscri is/was member of the following selection committees:
- Associate Professors: LORIA and University Côte d'Azur
- Nathalie Mitton was member of the following selection committees:
- Inria researcher: vice-chair of the junior researcher committee (CR) for Inria Lille and member of INRAE junior researcher committee (CR) and of Inria Senior researcher committee (DR2)
- Professor: Sorbonne Université and Université de Rennes.
- Valeria Loscri is/was member of the following selection committees:
11.3 Popularization
Alexandre Veremme and Carol Habib participated to the CHICHE programme.
12 Scientific production
12.1 Major publications
- 1 inproceedingsRobust Device Authentication in Multi-Node Networks: ML-Assisted Hybrid PLA Exploiting Hardware Impairments.Annual Computer Security Applications Conference (ACSAC)Waikiki, Hawaii, USA, United StatesDecember 2024HALback to text
- 2 articleHARPAGON: An energy management framework for attacks in IoT networks.IEEE Internet of Things JournalMay 2022. In press. HALDOI
- 3 articleFeD-TST: Federated Temporal Sparse Transformers for QoS prediction in Dynamic IoT Networks.IEEE Transactions on Network and Service ManagementNovember 2024HALDOIback to text
- 4 inproceedingsMachine Learning Approach for Mobility Context Classification using Radio Beacons.Proc of 31st International Symposium on the Modeling, Analysis, and Simulation of Computerand Telecommunication SystemsMASCOTS2023 IEEENew York, United StatesOctober 2023HALback to text
- 5 articleAdaptive HELLO Protocol for Vehicular Networks.ITU Journal on Future and Evolving Technologies2024HALback to text
12.2 Publications of the year
International journals
Invited conferences
International peer-reviewed conferences
Scientific books
Doctoral dissertations and habilitation theses
12.3 Cited publications
- 27 inproceedingsAutomated and Reproducible Application Traces Generation for IoT Applications.Q2SWinet 2021 - 17th ACM Symposium on QoS and Security for Wireless and Mobile NetworksAlicante, SpainACMNovember 2021, 1-8HALDOIback to text

